A large portion of this section is going to be dedicated to explaining various types of malware. The reason for that is that the term malware is used to describe a massive category of threats, and these threats are constantly evolving. Just as soon as companies find ways to detect and prevent a certain type of malware, malicious actors adjust their tactics to evade those detections and preventions.
What’s malware?
What is malware in the first place?
Malware is software designed to do something malicious. The word comes from combining malicious + software.

It’s a massively broad categorization, and so there are all kinds of various types of malware that come in different shapes and sizes, and that are designed for different purposes.
In this section, we’re going to explain a variety of different types of malware, what makes them different, and when or why they’re used by adversaries. We’ll also explain ways of defending yourself, your resources, and your organization’s resources against these malware threats.
As I was creating this lesson and this section of the course, it really dawned on me how malware categorization is all over the place. Even if you ask experts in the industry, you’ll eventually start to get different answers to some of the same questions.
The reason for that is that there are surprisingly few standards that have been created to categorize malware. Or they’re older and no one’s really updated them. So everyone’s kind of doing their own thing, which can make understanding malware and the different types more complicated than it should be.
Types of malware
So let’s start by taking a look at a few malware types, that way we can try and keep a general structure in mind as we study. Keep in mind that many of these also have their own sub-categories:
- Trojans
- Downloader trojans
- Backdoor trojans
- Rootkit trojans
- Remote Access Trojans
- Etc…
- Viruses — that’s right, viruses are a form of malware, even though sometimes people describe them as if they’re separate threats
- Worms
- Crypto-malware
- Ransomware
- Spyware
- Keylogger
- Adware and Malvertising
- Rootkits
- Macro malware
- Browser Hijacker
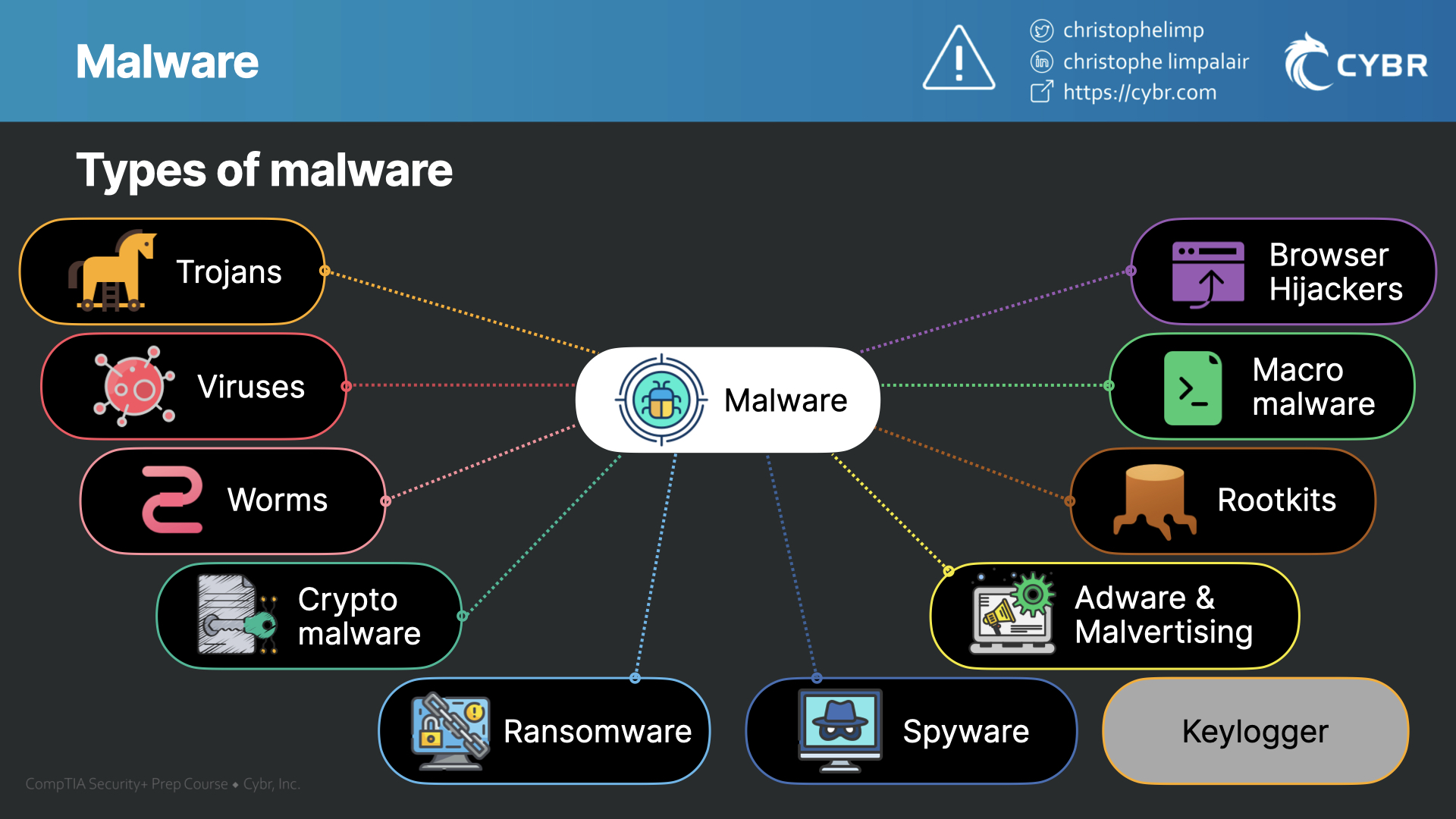
This is not a fully comprehensive list of all malware, and frankly, I’ve never seen a list that I would consider comprehensive that has been made publicly available. But also, for the exam, these are the main categories that we need to know about.
So all of these categories are technically called malware, because they are designed to do something malicious. That is their purpose for existing.
How does malware spread?
Just like there are different categories of malware, there are also different ways that malware spreads.
Here are some of the most common:
- Drive-by downloads — this happens when malware gets downloaded to your device without you realizing it. Perhaps you’re visiting a website, and as you open the page, the malware automatically downloads. This is usually caused by a browser, application, or operating system vulnerability
- Spam and phishing — while spam and phishing may not always contain malware, it can be used to send fake attachments or link to downloads that do contain malware
- Vulnerabilities — vulnerabilities are security defects in software that can be leveraged by an attacker to deliver and/or execute malware. We already touched on that a little bit, but this could be through a web application vulnerability, a desktop or mobile app vulnerability, or even through an operating system vulnerability
- Software bundles — malware can also sometimes be installed accidentally via software bundles. This happens when you are installing a piece of software from the Internet, and at the same time, that software is installing malware. This is even more common with pirated software
- Malvertising – which uses online advertisements to spread malware
These are techniques that can be used to initially infect a device. Once a device is infected, malware may try to spread to other devices, or it may just stay put and perform more actions on that specific device. It depends on what type of malware it is, and what it’s designed to do.
What are some common signs that your device is infected with malware?
Once a device is infected, it can either take a very long time to realize it (if you ever even realize it), or it can become apparent right away. Usually, if the malware is pervasive, you will notice things like:
- Slower computer or network performance
- Software that was installed on your device and that you don’t remember installing
- Emails that are being sent out from your inbox that you never sent
- Social media posts that are being sent out that you didn’t write
- You may see advertisement on websites that shouldn’t have ads, or even ads popping up while you’re not navigating the web
- Your browser redirects you to websites that you didn’t type in
- Certain operating system functionality gets disabled randomly
- You get locked out of your device, and potentially asked for a ransom
These are some of the most common signs. But keep in mind that well-designed malware or malware that is intended to remain stealthy could very well remain hidden and could continue to remain hidden on your device for a very long time.
Just because you have anti-malware software installed doesn’t mean your device is free of malware.
How can you defend against malware?
Speaking of anti-malware, let’s wrap up this lesson by talking about defenses against malware.
- Anti-malware and anti-viruses – while anti-malware won’t prevent or find all malware, it can help and should be part of your defense strategy. Make sure you keep anti-malware and anti-virus software as up-to-date as you can
- Keep your operating system (and other software) up-to-date – along similar lines, you should keep your OS and applications as up-to-date as you can. People constantly find vulnerabilities in code, so developers have to react by patching those vulnerabilities and sending out updates to their users. If you don’t patch your application when you receive those updates, you’re keeping your device vulnerable to attack
- Be cautious of email attachments or links – attachments could be malware, and links could take you to phishing websites or vulnerable websites that may attempt a drive-by download
- Don’t visit shady websites – especially on work devices, but also in general. Not only do you not know who is running the website and they could have malicious intent, but even if the website itself is legitimate, it may have vulnerabilities that end up getting exploited by someone who is malicious
There are other tactics we can use to defend against malware, but the ones we just talked about will apply to most malware types, and so as we progress through this section, keep them in mind.
Conclusion
Now that we’ve gone through an introduction of malware types, methods of infection, and defenses, let’s complete this lesson and move on to the next!


Responses