Multifactor authentication (MFA) factors and attributes

Password-based authentication has been proven time and time again to be a vulnerable form of authentication. One of the best defenses is using Multifactor Authentication, or MFA, and its factors as well as attributes.
MFA is when you are using two or more different factors to achieve authentication…sometimes you may see it called 2FA (2 Factor Authentication) when we are using just 2 factors, but technically MFA can mean two or more, so it can also be used to mean 2FA. That makes 2FA a subset of MFA.
As an example, instead of just requiring a username and password combination, we may now also need to provide a one-time password sent via SMS (those codes you get via text message). That way, even if an attacker has the correct username/password, they still can’t authenticate unless they also have access to the one-time password that was sent to you.
One-time passwords are just one of many examples, and to achieve proper MFA, we need to use different factors as well as attributes.
Some of those factors and attributes are considered to be more secure than others, which we’ll also touch on in this article.
This post was taken from one of the lessons in our CompTIA Security+ preparation course. This is a topic that you will be tested on if you sit for this exam, so make sure you understand it well!
MFA Factors
The name multifactor authentication literally tells us that there should be multiple factors used for authenticating a user or system, but what are those factors?
There are 3 categories of factors that we need to know like the back of our hand:
- Something you know
- Something you have
- Something you are
Something you know
The something you know factor is one that we are most familiar with, and it’s a commonly used factor of authentication. This can be anything from:
- Passwords
- PINs
- Security questions

Anything that could be considered knowledge that only you should have falls under the something you know factor. It’s knowledge stored in your head or somewhere else secure like a password manager.
Something you have
Next, we have the something you have factor. With this factor, instead of asking the user to provide knowledge that only they would know, we’re asking them to provide data that only they would have physical or virtual access to.
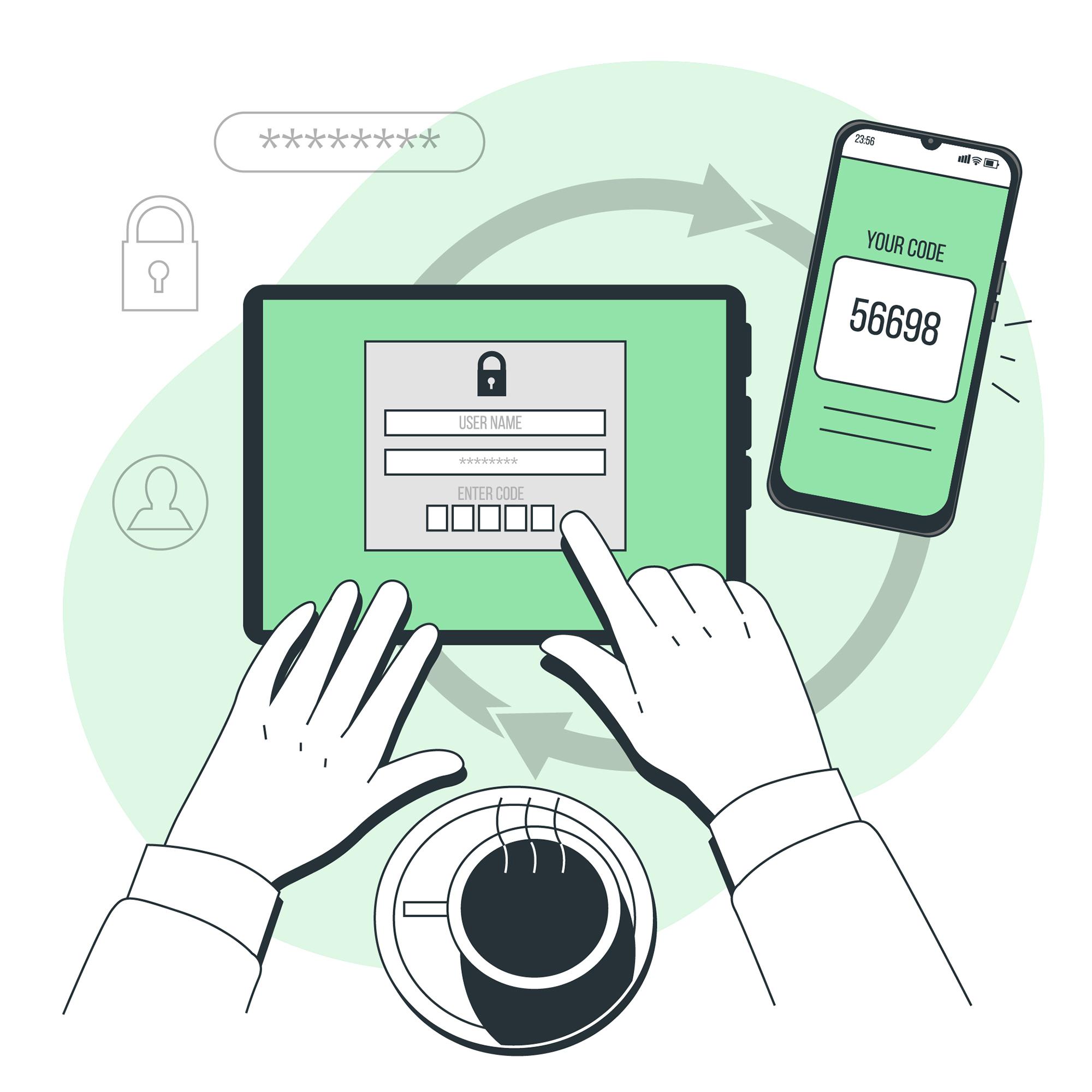
This can be anything from:
- Push notifications (typically through mobile applications, which means they need to have the application installed on their device, and they need to be able to unlock that device)
- PIN codes sent to you via SMS or email, also known as one-time codes
- Authenticator apps (either software or hardware-based) which provide:
- Tokens
- One-time time-based codes
- Smart cards, such as:
- Personal Identity Verification (PIV) cards for U.S. federal agencies
- RFID or NFC cards and key fobs
- Phone calls

Something you are
The third factor is something you are. Instead of asking a user to provide knowledge that only they should have, or to provide data that only they should have access to, we’re asking them to provide information that only they have biologically.
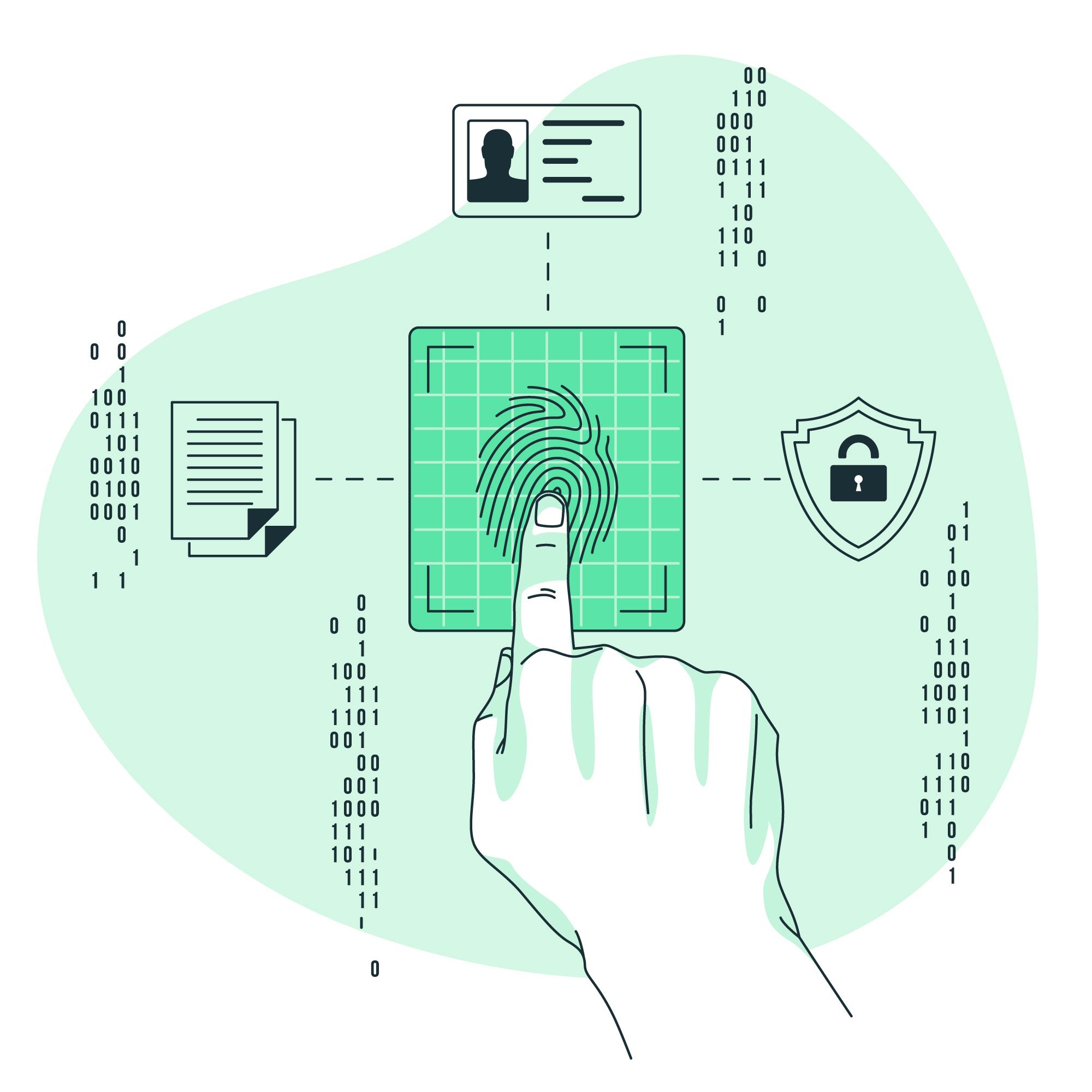
This could be anything from:
- Fingerprint scans (such as TouchID)
- Iris scans (this is the colored part of your eye surrounding the pupil)
- Retina scans (this is behind the iris)
- Facial identification (such as FaceID)
- Voice identification (speech)
- Vein identification (such as palm vein recognition)
The something you are factor can use biometrics as another layer of authentication to prove that the person trying to authenticate really is who they claim to be.
Just a quick note here: artificial intelligence has become very good at mimicking voices, making the voice identification factor an increasingly weak one.
Why MFA factors matter, and examples of proper implementation
Each of the three factors increase in complexity — both to implement and to fulfill.
Something you know is the easiest to implement but it’s also the weakest factor. Something you have is a little bit more difficult to implement but stronger. Something you are is the hardest to implement but it’s also the strongest authentication factor.
A lot of times, you will see applications only use one factor of authentication. They will ask you for a username and password, and then they’ll ask you to answer security questions that you had created at the time of registration. This is technically not multifactor authentication, because you are using the same factor: something you know. So you’re actually only using singlefactor authentication in that case!
Instead, to achieve MFA, you have to have at least two of those factors implemented.
Most of the time, that’s going to be something you know and something you have. For example, it could be:
- Something you know: A username and password, plus
- Something you have: A one-time password from an authenticator app
Or:
- Something you know: A username and password, plus
- Something you have: An SMS one-time code
If you are trying to authenticate in order to enter a building, you may have to provide:
- Something you know: Enter a PIN code assigned to you, plus
- Something you have: Use an RFID key fob
All of these examples are examples of 2FA since they’re only using two factors to authenticate. Again, this can still be called MFA, but if you see 2FA on a certification exam like the Security+, I want you to know what that means which is why I’m repeating it. There’s also some confusion that I’ve seen on the Internet when it comes to that.

If, with our last example, we want to add a 3rd factor of authentication, we could have it be:
- Something you know: Enter a PIN code assigned to you, plus
- Something you have: Use an RFID key fob
- Something you are: Retina scan
Or, with many phones nowadays, apps sort of assume that you’ve already provided one factor such as something you are (with FaceID or fingerprint), or something you know (with a PIN code), and so they’ll either piggyback off of that by asking you if you want to use FaceID or fingerprint recognition to login to the app, or they’ll ask you to provide the username/password, plus something you have (like an SMS code or authenticator app code), plus FaceID or fingerprint.
MFA Attributes
In addition to those MFA factors we just discussed, there are also MFA attributes, and they are:
- Somewhere you are
- Something you can do
- Something you exhibit
- Someone you know
These attributes can be used in addition to factors for increased defense in depth. Sometimes they are used to replace factors, but in most cases, they’re used in addition to factors.
Somewhere you are
With somewhere you are, we can check the authenticating user or system’s location. You’ve probably experienced this one in the past: you usually authenticate to a service from your home location, but then one day, you travel to a different city, state, or country, or even just use a VPN, and as you authenticate to that service, you get a notification from the service asking if it’s really you.
That service kept track of your geolocation, typically using your IP address, cookies, or phone tracking, and if it notices a big enough difference, it triggers a security event.

A system could even be designed to detect the feasibility of whether someone could have been in two separate locations in a certain period of time. So if you authenticate from the state of Georgia in the USA, and then 2 hours later you try to authenticate from the country of Greece, then that would be suspicious because there is no viable technology on earth that could let someone physically travel that quickly. Either you used virtual technology such as a VPN to change your virtual location, or someone that shouldn’t be is trying to authenticate with your credentials.
The somewhere you are attribute can help determine that.
Something you can do
The next attribute is something you can do. This is an attribute that has to do with authenticating via gestures. This could be waving a certain way, it could be clicking or tapping in a certain pattern, or things like that.
An example is called Picture Password, which was a feature introduced with Windows 8. You could create three different gestures on an image of your choice, and that gesture would then be used as a way of authenticating.
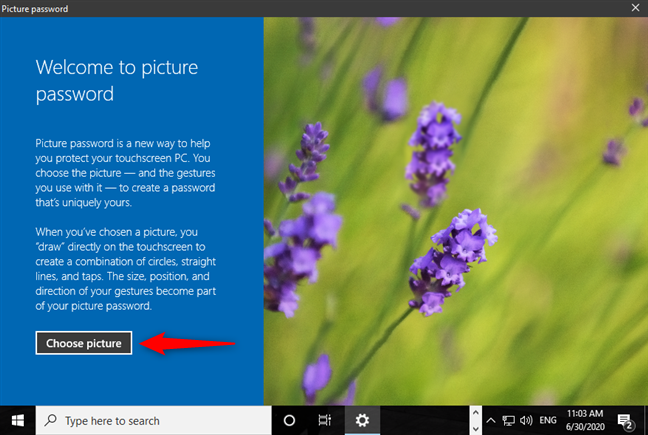
It could be a combination of making circles with your mouse, going in a straight line, or even clicks/taps in certain locations or patterns.
Another example of this is something we are very familiar with and see being used all of the time: signing documents. If you are able to accurately reproduce a signature, then that could be used as authentication.
Something you exhibit
Something you exhibit is a bit more tricky to define and use, because it relies on particular personality traits or even neurological behaviors.
Maybe it’s the way you talk, walk, or act. If, one day, you started acting differently, then that could be an indication that someone is trying to impersonate you because you are not exhibiting natural behaviors.
Someone you know
Someone you know is the final attribute that we’ll talk about.
An example of this would be if you were trying to enter a corporate building. You will likely be asked to sign an entry log and provide a photo ID, but that alone wouldn’t be sufficient. Just because you provide those things doesn’t mean a security guard will let you in.
However, if a trusted employee came down to the lobby and vouched for you by saying you had a scheduled meeting, then the security guards would likely let you in because of someone you know.
MFA Factors vs. Attributes
Attributes are usually considered to be more “fluid” than factors. They’re usually not as black and white as compared to factors, but they can still be used in addition to authentication factors to verify whether someone should be authenticated or not.
Attributes by themselves aren’t considered factors because on their own, they do not confirm a user’s identity. With that said, in combination, they can absolutely help improve security when it comes to authenticating a user or system.
Conclusion
As I said at the beginning, these are very important concepts for you to understand, because you will be tested on them if you sit for an IT/cybersecurity certification exam. Not only for the Security+, but in most (if not all) of IT exams that you take throughout your career.
It’s also just generally good information to know because it will help you secure your accounts, and if you ever need to implement an authentication system (like say, for a personal project), you’ll know what’s important.







Responses