Are your passwords strong enough?

In this digital day and age, most of us know what a password is. If you’ve found this article or any other like it, you likely have a social media account, an email, or somewhere you store pictures and documents. These all require passwords. Most of these platforms have requirements for what the passwords should look like. The requirements could be a specific password length, the presence of different numbers or symbols in the password, or even that the password cannot be something easy to guess. This is done to prevent people from accessing your information.
Have you ever stopped to wonder why different platforms have different requirements? Or why they force you to have certain characters or password lengths in the first place?

In this article, we’ll talk about what makes a password strong, and why sometimes passwords just aren’t enough to fend off attackers. To start, we first need to discuss some potential techniques that attackers may use to figure out what your password is.
Examples of techniques used by attackers to crack passwords
To better understand how to keep strong passwords, we need to understand the various techniques through which malicious hackers can use to get access to your passwords:
Physical access
If a criminal can physically touch a computer, they could do a lot of damage. They could even get information from the surroundings of that computer. Several forms of physical access include:
- Shoulder surfing: someone sees you typing the password and later replicates it
- Someone steals the diary/log/journal where you have written down your passwords.
- Someone forgets to lock their computer before walking away
- Etc…
Brute Force attack
This is the simplest but the most time-consuming technique that hackers use for obtaining passwords. This is mostly used when every other password cracking technique fails. Here the password cracking programs try to use every possible combination of words, numbers, letters, and special characters (like @!@#$%^&*) to crack the password. This technique may not be very practical if the password contains different types of characters (e.g. lowercase letters, UPPERCASE LETTERS, Numbers from 0-9, Special Characters like @!@#$%^&*, etc), or if it’s relatively long. Nowadays, the only time brute force attacks may work is when the attacker is using a rule-based attack, where the attacker can predefine some rules to the program, such as the length of the password, the number of upper case/lower case characters, the number or type of special characters, etc…but even then, the sheer volume of attempts typically makes brute force attacks impractical, especially if they have to be performed over a network (such as on a website) since that will also add latency.
Dictionary attack
In a dictionary attack, which is a type of brute force attack, the attacker uses a dictionary of commonly used passwords and runs them through a password cracking tool. This is much better since it tests for only a list of the most commonly used passwords. Here’s a quick mental exercise for you: how do you think attackers find out the most commonly used passwords by people? By the way, here’s an example of a dictionary list of the most common passwords.
Rainbow Tables
Let’s assume you have an account with company X which stores their passwords in a hash format.
If you’re not familiar with hashing, here’s a quick explanation: nowadays, most applications don’t store user passwords as a plaintext (human-readable format) in their databases, what they do is take the human-readable plaintext passwords and hash them with an algorithm. According to NIST, hashing is the process of using a mathematical algorithm against data to produce a numeric value that is representative of that data. (NIST Glossary)
Whenever you log in with a human-readable plaintext username and password, their system uses an algorithm to convert your plaintext password into its hashed equivalent and tries to match it with the pre-existing hashed password on their database. If they match, then you are logged in. Now let’s say that somehow company X’s password database gets leaked. The first thing hackers will do is run the leaked hashes through a rainbow table. A rainbow table is a table containing a list of passwords and their corresponding hashed form of the password.
Credential Stuffing
Because many people use the same password for different sites, if the attacker somehow gets your credential from company X, they can use that to try and log in to your other accounts (banking, social media, email, etc…). If they are using the same credential, then they will be able to get access to those other systems. This is called a credential stuffing attack.

Choosing strong passwords
We just went through a list of a few password attacks to demonstrate that there are many avenues through which an attacker can figure out what your password is. For some of those attacks, it doesn’t really matter how “strong” your password is (ie: with shoulder surfing), while for others, it can make a big difference (ie: with brute force attacks).
Since this article is focusing on password strength, the question becomes: what’s the best way to choose a strong password?
When it comes to password strength, people typically talk about two main factors:
- Password length, and
- Password complexity
Password length
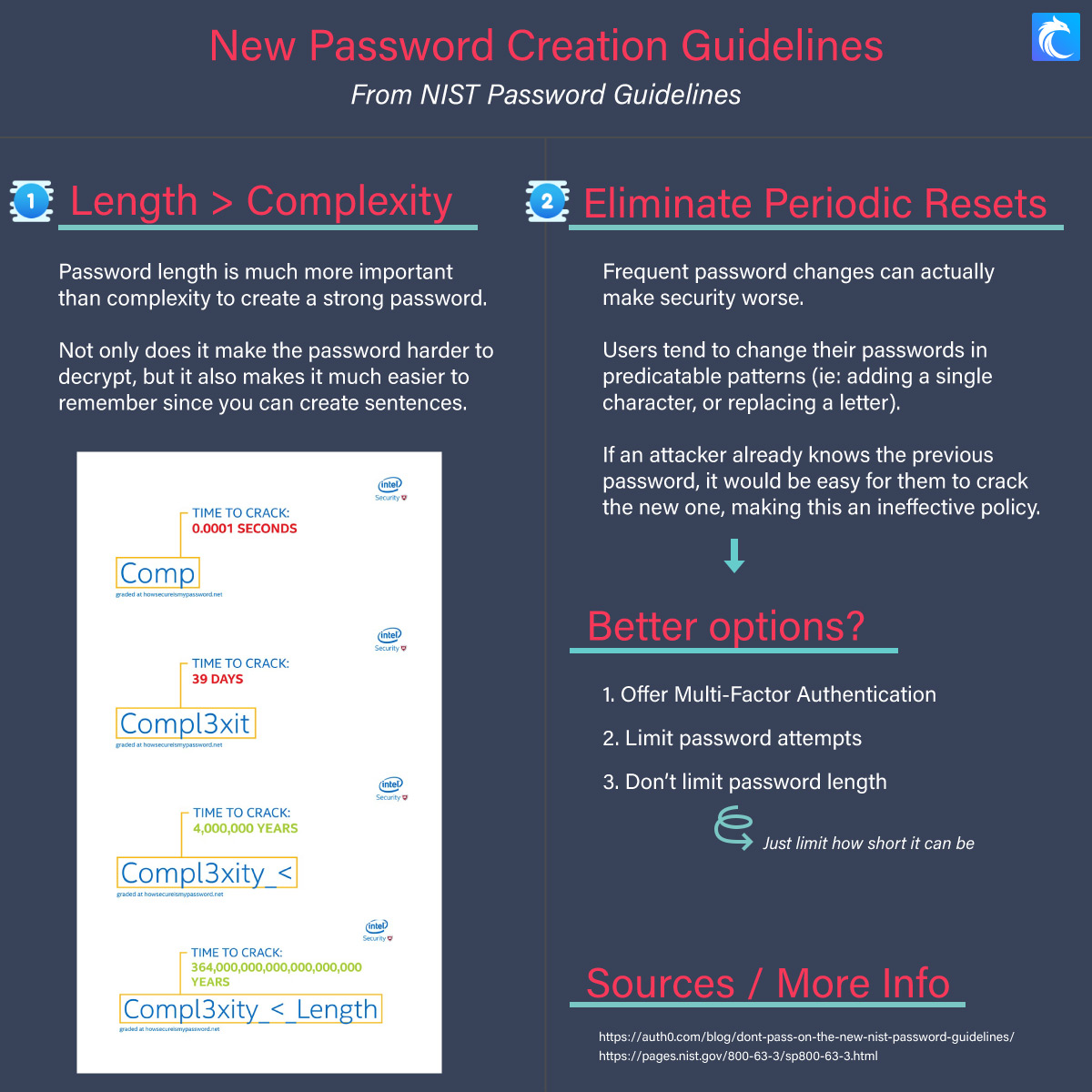
Password length is the most important factor in determining password strength, and we’ll explain in more detail why in just a moment.
Length especially matters when the attacker is running various types of brute force attacks. If your password is 8 or fewer characters, it can be brute-forced relatively easily, especially by powerful machines. The best password recommendation is to use memorable sentences because they will 1) be much longer that way, and 2) be much easier for you to remember.
Password complexity
Passwords with higher complexity (the amount of varying information in it, like uppercase, lower case, symbols) are relatively safer, but only when combined with password length. Password length is far more important than password complexity, and in fact, complexity usually just makes passwords harder for people to remember, so it is not recommended unless you’re using a password manager (and that is recommended).
Length vs. Complexity
XKCD’s site created an image that answers the question of which is best between length and complexity, and we think it’s one of the best ways to visualize it:

From the image above you can clearly see that using a short password and replacing some letters with a special character increased complexity, but it’s harder to remember.
Instead, using four common long words decreased the complexity of the password, but made it significantly harder for an attacker to crack because of its length. Even though it is using common words, which are susceptible to dictionary attacks, it would still take a very long time to crack the password due to its length, which is why length is so much more important in generating strong passwords.
Which of these methods ensures better security?
Lucky for us, some smart people came up with the idea of password managers. One of the main challenges of coming up with strong passwords is that we’re afraid we’ll forget them. So we end up shortening them or using everyday objects or people that we’re close to. Or we write them down on sticky pads next to our monitors. All of these things introduce major weaknesses to our passwords.
Instead, password managers:
- Remove the need to remember passwords (except for one main password to access your account)
- Automatically generate strong passwords for you
- Generate unique passwords for every account you have
- Provide you with a way of sharing access to others without displaying the password
The way that they generate strong passwords is by following these rules:
- DO use a combination of UPPERCASE, lowercase, numbers, and special characters.
- DO NOT use passwords of short length (should be at least 8 characters long).
- DO NOT use common words as passwords.
- DO NOT use your name, date of birth, or other identifying information as your password.
Apart from those, they also help with following these rules:
- DO NOT use the same passwords across multiple websites.
- DO NOT share your passwords with others.
- DO NOT write down your passwords anywhere.
Here a point needs to be made that you won’t be able to remember such “strong passwords” for different websites and that’s where password managers can help you. Read more about password managers here.
Multi-Factor Authentication
Everything that we’ve discussed up until this point has been regarding making passwords stronger…but even if we have the strongest password in the world, our accounts can still end up compromised, and for many reasons. Some of which are completely out of our control.
Maybe the organization storing your passwords didn’t store hashed versions of passwords and instead stored the plaintext version, and a malicious actor got their hands on this database.
Maybe you’re using public WiFi that doesn’t properly encrypt communications with a platform you visited and logged into.
Or, maybe you fell for a phishing attack and typed in your password on a fake login form.
Whatever the reason, the strongest password in the world won’t help you against those attacks.
That’s why the Internet is (slowly) moving towards either passwordless authentication or some form of Multi-Factor Authentication (also known as MFA).

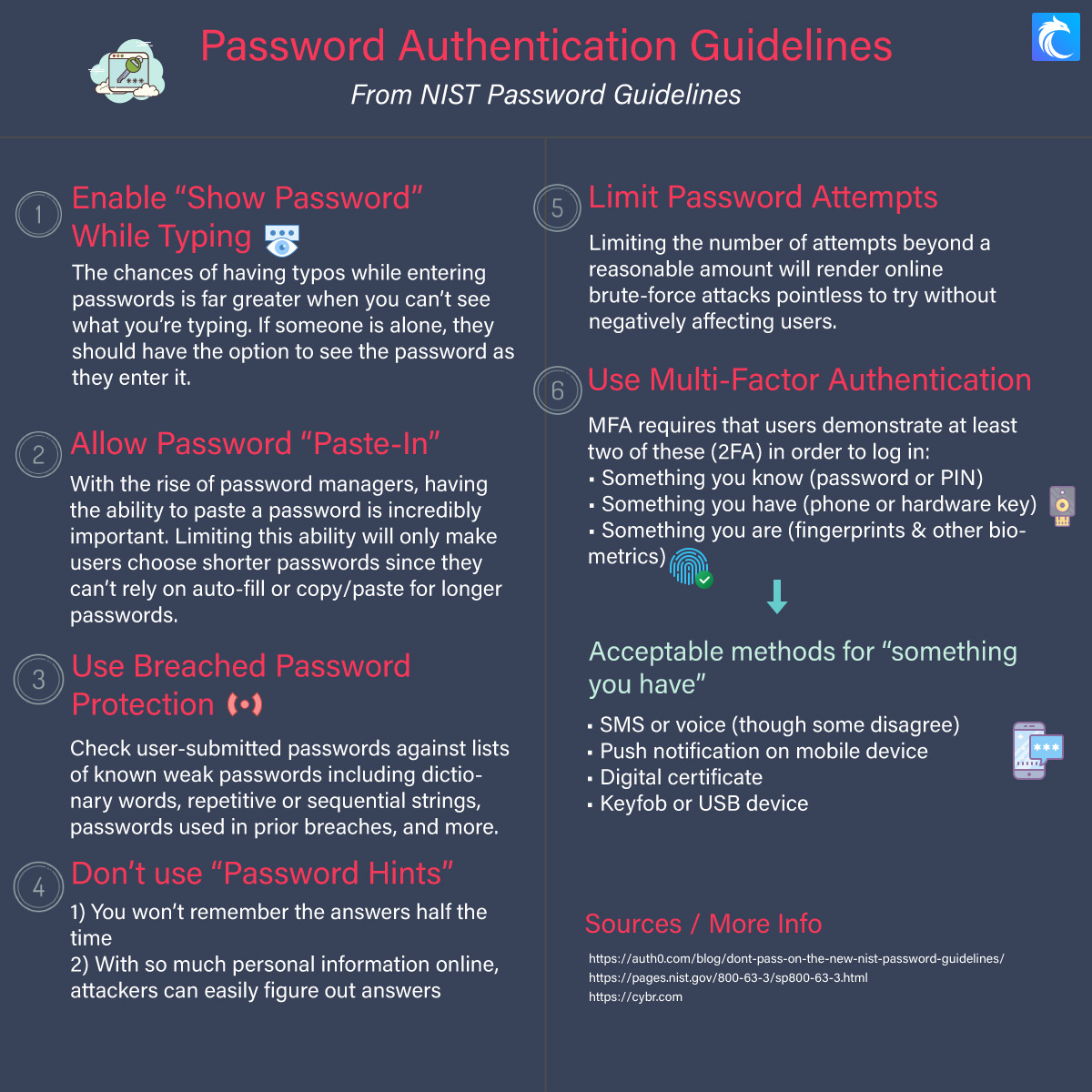
Multi-Factor authentication is “an authentication system that requires more than one distinct authentication factor for successful authentication. [It] can be performed using a multifactor authenticator or by a combination of authenticators that provide different factors.” (NIST Glossary)
An easy way to remember what multi-factor authentication entails is by remembering what the authentication likely needs of you: something you know, something you are, something you have.
- Something you know: A password or PIN, one of the most common forms of authentication.
- Something you have: A token given by the company that holds your account. Often used for sensitive information as the second form of authentication in conjunction with the other two. This token can be a code that changes every so often or a card with a QR or barcode that has information about you.
- Something you are: a biometric scanner that uses fingerprint or facial recognition. This factor is usually either used as a 3rd factor after both something you know and something you have, or to replace passwords. For example, most phones and laptops offer the chance to scan your fingerprint or face to access your phone instead of entering a password.
Two-Factor Authentication uses one or more of these to ensure that a password is not the only way to access an account. Typically, this form of authentication uses Something You Know and Something You Have (password and an access code from a text or an app) or Something You Know and Something You Are (password and fingerprint or facial recognition scanner). Rarely are all three used for the same account, unless you are dealing with highly sensitive systems or information.
Password cheat sheets
To help keep track of best practices when it comes to generating, using, and even storing passwords as both users and as developers, we’ve created three different cheat sheets that follow the NIST Password Guidelines:
New Password Creation
Password Authentication
Password Storage

Conclusion
In this article, we talked about passwords. We discussed what a good password looks like, offered some tips to make them stronger, and left you with some tools to protect your account. Hopefully, these tools will prevent an account of yours from being accessed without your permission. We can’t win every battle we choose, but we can make the opponent regret picking us by making it much harder on them!
This article was originally published on TheCyberCops.com by Amandeep, and re-published on Cybr with permission. Edited by Sorrel and Christophe.







Responses