Network Access Control (NAC)
In our course, we talk about Zero Trust and how it’s an approach that believes in continuously checking access and policy violations, even within internal networks. An important part of achieving this is to check devices that attempt to connect to our networks. We can do that with Network Access Control or NAC.
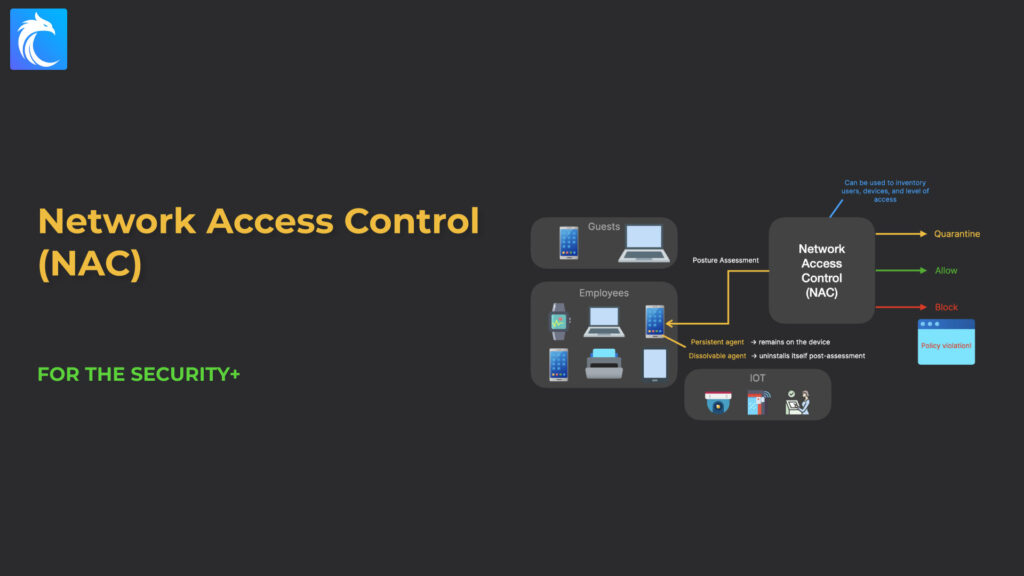
With NAC, we can prevent unauthorized users or devices from gaining access to a private network without first going through an assessment that verifies authentication and compliance with security policies.
There are three concepts related to NAC that you need to understand for the Security+ exam:
- How NACs differ from firewalls
- NACs for endpoint management
- Posture assessments
Let’s get into it.

NAC vs. Firewall
Using NAC is different from using firewalls for a number of reasons.
For one, firewalls are typically used to control the flow of traffic between networks or on hosts. If we have two separate networks connecting together, that connection point will likely have a firewall in between. Or, if we have a connection to and from the open Internet, we’ll want to make sure we have a firewall protecting that entry point.
NAC, on the other hand, is used to control communication between endpoints within a network. If you have two computers on the same subnet who are exchanging files, network access control can control this file exchange. Or, if you have a device attempting to connect to a network, NAC can evaluate it first before allowing it to join that network.
Firewalls also usually control traffic through a set of rules. Those rules, once set, are fairly rigid. They can be updated over time, but for the most part, they stay the same.
In NAC, we can use multiple criteria to evaluate access. In fact, devices are organized into groups, and as the device’s behavior and attributes change, their group membership can also change. Each of those groups is linked to a security policy that dictates a certain level of network privilege.

NAC for endpoint management
Another way to think of it is that the NAC acts on the endpoints, while firewalls control traffic flowing in and out of networks…this also means that they complement each other by addressing different parts of network control.
Because NAC’s main goal is to control and manage the use of non-compliant end-user devices that are connecting to our networks, it can be particularly useful in today’s day and age where users can bring in all sorts of devices within our networks.
We call this BYOD, or Bringing Your Own Device. Examples include non-company phones, tablets, laptops, smartwatches, etc..

Even IoT devices sometimes need to be connected to a network. For example, you may have sensors, security cameras, or check-in kiosks. Those sorts of devices would have very different access levels than an employee’s smartphone.
We have no way of knowing what’s happened to those devices or if they’ve been infected with malware, but we want to keep that off of our networks.
Posture assessment
To know whether an external device should be allowed to connect or not, we have to perform a posture assessment.
First, we can check to see if it’s a device that’s already been allowed on our network or not.
Second, we can check to see if the device is running any acceptable anti-malware software or not.
Third, we can check to see if it’s running any other company-required software or not.
To have that level of visibility, we need to be able to run software on that device. One approach is to use a persistent agent, which is an agent that would remain on the device and be activated each time the device connects to the network.

An alternative is a dissolvable agent. Whenever the device connects to the network, the software runs on that device to perform the assessment. Once the assessment is complete, the software uninstalls itself from the device.
While the device is being assessed, it’s usually placed in quarantine to prevent it from getting access to the internal network. Once the assessment is completed, if the device meets policy, then it will be allowed in the network. If any of the requirements aren’t met, we can provide the user and device with a web portal that explains which policies they are violating and how to correct that violation.

This also means that NAC can be used as an inventory of users, their devices, and the level of access they have.
Conclusion
Network Access Control is an important part of securing networks. Make sure you understand some of the differences as compared to firewalls, what NAC is used for, and the general concepts of how posture assessments work. We also want to make sure that you understand the differences between a persistent and dissolvable agent.






Responses