Key stretching concepts and algorithms

One of the best ways to make a password strong is to make it long. The longer the password is, the harder it is to crack, especially when we’re using a strong encryption algorithm and hashing with salting.
The problem with this is that you have no idea what kinds of passwords your users will use, and unless you enforce a lengthy minimum password requirement, which will frustrate users, then you may end up with shorter passwords stored in your database.
Key stretching is a technique we can use to make weak keys — in our case passwords — more secure by “stretching” them out.
Prefer learning by watching videos instead of reading?
This lesson is pulled directly from our CompTIA Security+ certification preparation course.
Key stretching
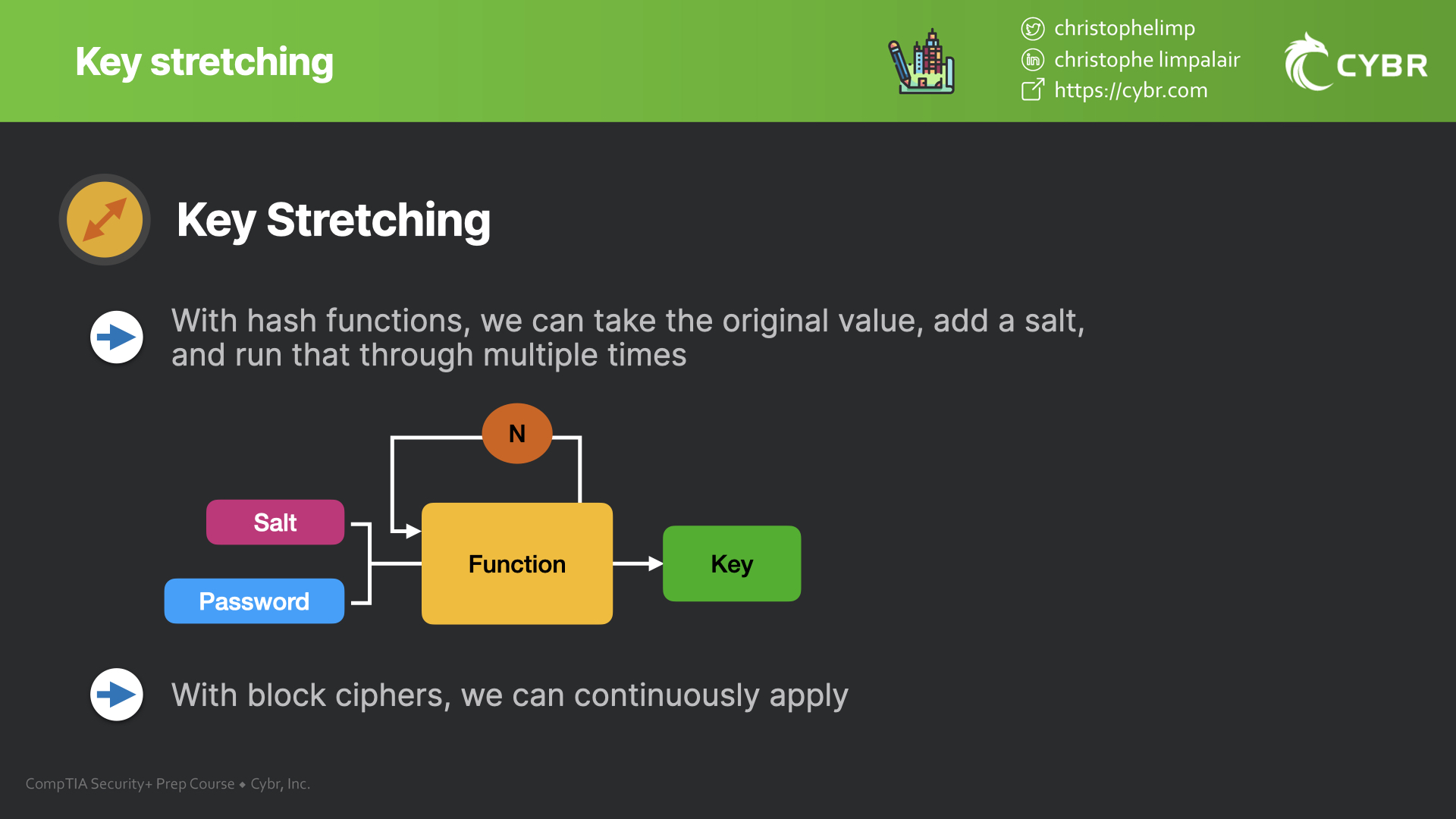
There are several ways of achieving key stretching, including using hash functions, or applying block ciphers. We can also add salt values to defend against hash or rainbow table attacks.
With hash functions, we can take the original value, add a salt, and run that through functions multiple times. So you could hash a value, then hash the hashed version of that value, and so on…
Or we could apply block ciphers over and over again — but we’ll talk about block ciphers in a separate post.
There are two widely-used key stretching algorithms which are:
- Password-Based Key Derivation Function 2 (PBKDF2)
- bcrypt
PBKDF2
PBKDF2 is part of PKCS #5 v 2.01, which is a Password-Based Cryptography Specification, and it’s used to reduce vulnerability to brute-force attacks.
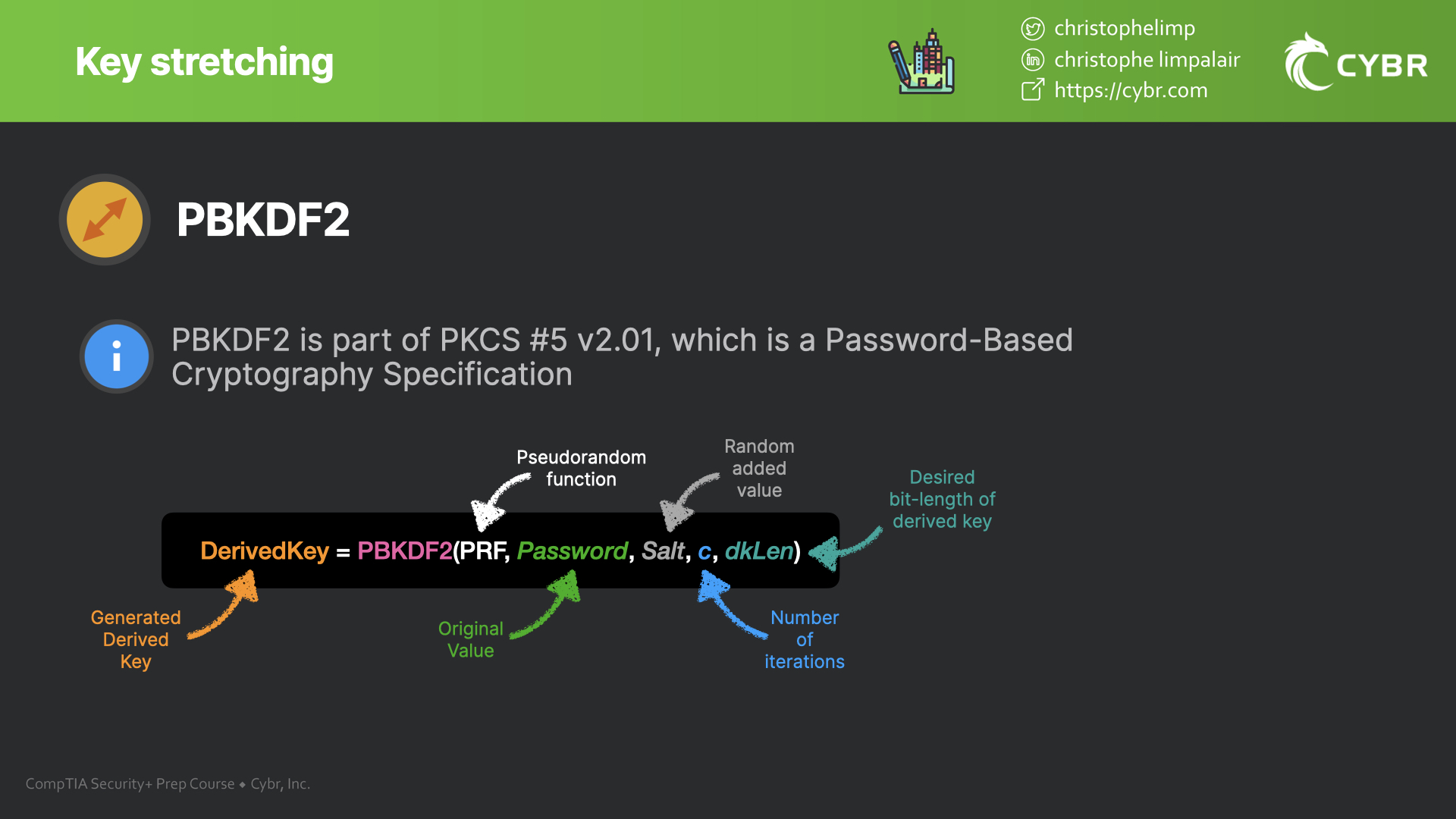
It applies a pseudorandom function to the input password along with a salt value, and it repeats this process multiple times to produce a derived key. That derived key is then what gets used as a cryptographic key.
As we see from the graphic above, we produce a Generated Derived Key by applying a Pseudorandom Function to the original Password and Salt value. We can also specify the Number of Iterations and Desired Bit-Length of the Derived Key. You do not need to know this equation for the exam, but visual learners may find this helpful in understanding the concepts.
bcrypt
bcrypt is based on the Blowfish cipher. It also uses a random salt value and it runs through multiple rounds to generate a stretched output.

As you can see from the graphic above, we produce a Hash value by applying a hash function that takes in the following values:
plainText-> this is the original password value, for examplesalt-> random salt valueiterations-> the number of iterations (increase this to increase cost)
A benefit of bcrypt is that we can modify the iteration count to make it slower to compute, which means that we can scale bcrypt as computing power increases over time and as malicious actors get access to faster machines.cc
Key stretching recap
Overall, you are essentially mimicking a longer key length by passing it through multiple iterations, even if the original key being used is quite short. In addition, you’re adding in a salt value to protect it against hash-based attacks such as hash table and rainbow table attacks.
Conclusion
Whenever you think of key stretching, think of it as taking potentially shorter key lengths and using an iterative process either through hashing or through block ciphers in order to mimic a longer key length.






Responses