TikTok spying on its users and massive security issues?

I woke up the other morning to a Forbes article with some pretty serious claims against TikTok, and I’ve been seeing other recent posts talking about TikTok spying and security issues, so it piqued my interest.
TikTok banned by US military, India
TikTok, in case you’ve been living under a rock, is one of the fastest-growing social media platforms in the world which allows users to create short videos with music and filters, and clearly it’s addictive because their growth has been at break-neck speeds.
According to an Oberlo report, TikTok has approximately 800 million users worldwide and has had over 1.5 billion downloads. That’s right, close to a billion users and over a billion downloads for a platform that was only launched in 2016.
What’s more, roughly 41% of TikTok users are aged between 16 and 24, and they were hit with a $5.7 million fine to settle allegations that it illegally collected personal information from children under the age of 13, such as names, email addresses, and their location.
Recent reports are sounding more major alarms about TikTok spying and security issues.
The U.S. Army & U.S. Navy banned TikTok on military devices because of its growing concerns over the app’s Chinese roots. They’ve even flat out called it a cybersecurity threat!
CheckPoint Research published a recent report with the title of “Is TikTok secure enough?” with detailed examples of vulnerabilities which the company claims to have fixed.
But, another even more recent report outlines how TikTok was caught spying on iPhone users in India and around the world after they had claimed to stop invasive practices back in April of this year…they say it was being used to stop spammers but stick around to see if you really believe that.
So what’s going on? What were or are those TikTok vulnerabilities, and how are they spying on their users?
Let’s take a look.
TikTok Security vulnerabilities discovered
The CheckPoint Research team discovered multiple vulnerabilities in TikTok and published them late last year and earlier this year which allowed attackers to:
- Get a hold of TikTok accounts and manipulate their content
- Delete videos
- Upload unauthorized videos
- Make private “hidden” videos public
- Reveal personal information saved on an account such as private email addresses
But how exactly could some of these attacks be carried out? Let’s see!
SMS Spoofing
One of the vulnerabilities is done through SMS Link Spoofing. Attackers could literally send SMS messages to any phone number on behalf of TikTok, that contains whatever link they want. So you could set up a phishing site, link to malware, or all-around get creative.
Here’s how it happens:
- You’d go to TikTok’s website
- You’d input a phone number and submit the request
- With a proxy tool like Burp Suite or OWASP ZAP, you capture the request being sent to TikTok’s servers
- You then modify that request before it gets to their servers, with literally any phone number you want, and any download_url you want
- You then proceed with sending that changed request to TikTok’s servers
- TikTok sends your beautifully crafted requeste to that phone number, and the user receives that link
- They click on the link, and BAM, you are now a master villain
Big no no.
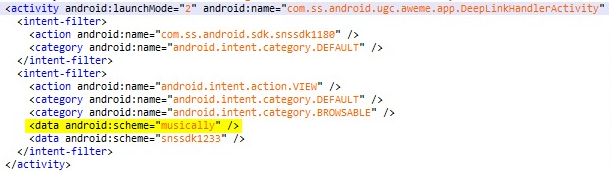
Deep Links vulnerability
CheckPoint also noticed, while reverse-engineering the TikTok app, that the Android version has what’s called “deep links” functionality.
So, if our SMS attack from earlier is successful, it would be possible to send a custom link that contains the vulnerable schemas, and the mobile app will open a browser window to go to the page you want them to go to, and when they go there, you would have access to that user’s cookies…
…Which is never a good thing because cookies can have a lot of private information not meant to be seen by others, and it also means we could now make requests on behalf of that user — essentially impersonating them.
Open redirection with domain regex bypass
Another vulnerability again has to do with sending out links, but this time we’re not just talking about links going through an SMS message. This could have been a link sent via any other method, like through Messenger, an email, or any other type of chat.
Imagine getting a link that looks like this:
https://login.tiktok.com/?redirect_url=https://newest-tiktok.comCode language: JavaScript (javascript)Most non-technical users would probably look at that and think nothing of it, especially if you promise them that it’s a brand new version of tiktok that isn’t publicly available yet. Who wouldn’t want to click on that?!?
(I wouldn’t because I don’t use tiktok, but anyway…)
The problem is, that https://newest-tiktok.com could be a domain owned by an attacker, NOT by TikTok, and users would get redirected to that website immediately after logging in.
Imagine that I’m the attacker and I own that domain. I could make the domain landing page look identical to TikTok’s login page, and I could put a message saying “incorrect username or password” and you would just think “ah crap, I probably missed a character again, let me type it back in.”
Except that error message was fake and designed to have you type in your username and password, which is then logged on my servers, and I now have credentials to your tiktok account.
This is possible because the login request was allowed to contain that redirect URL which was used to redirect users to their intended page after successfully logging in…TikTok developers had even put in a security control that was supposed to prevent an attack like this, but they used what’s called a ‘validation regex.’
(Is it pronounced reJEX or regEX? Tell me in the comments below)
Except, the regex they used was vulnerable because it was only looking for a value ending with tiktok.com, which is why we were able to have newest (or anything else really) – tiktok.com and it still work.
Cross-Site Scripting (XSS)
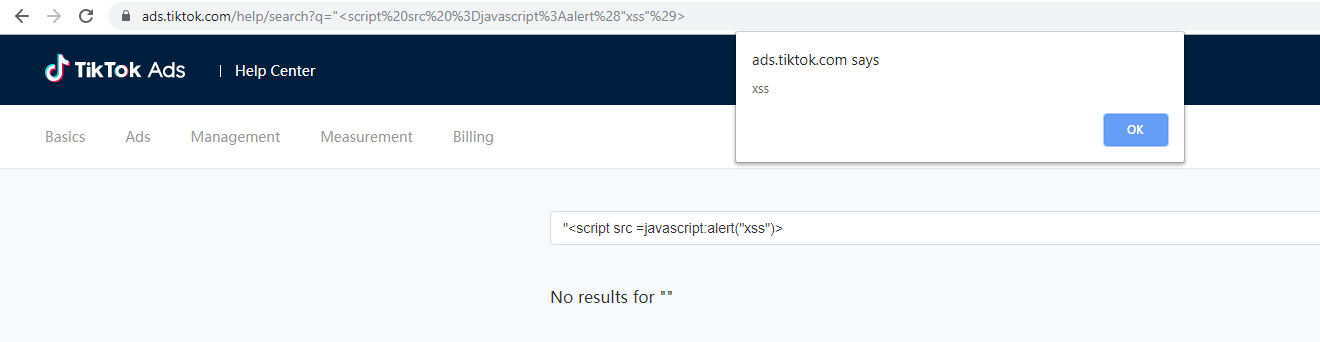
Next, Check Point Research found that one of TikTok’s subdomains – ads.tiktok.com – was vulnerable to XSS attacks, which lets an attacker input malicious scripts…
https://ads.tiktok.com/help/search?=%22%3Cscript%20src%20%3Djavascript%3Aalert%28%29%3ECode language: JavaScript (javascript)That looks like a bunch of gibberish, and it is, and again most non-technical users would ignore that and simply click on the link, when it reality it would execute this script:
“<script src=javascript:alert(“xss”)>Code language: HTML, XML (xml)In this case, all that does is create one of those annoying alert boxes that just writes out “xss”, but that’s just a proof of concept. In reality, an attacker could do far more damage like:
- Redirect you to one of those look-alike websites we talked about
- Send your cookies to the attacker’s server so they can hijack your account
- Or fun stuff like that
Cross-Site Request Forgery (CSRF)
The last few attacks we talked about set the stage for additional types of attacks, because now we can talk about vulnerabilities that make way to what’s called Cross-Site Request Forgery (CSRF).
By modifying requests via basic URLs:
https://api-t.tiktok.com/aweme/v1/aweme/delete/?aweme_id=video_idCode language: JavaScript (javascript)We can perform actions on behalf of that user, including:
- Deleting videos
- Creating videos
- Making hidden videos public
- Forcing a user to accept a follow request
And that would happen literally from you just clicking that link, no other action would be required!
Sensitive Data Exposure
One last vulnerability found and mentioned in this report can make use of the Cross-Site Scripting attack we talked about previously, because an attacker could inject their malicious script, and then have that script make a call to TikTok’s servers via one of their APIs, which would grab the user’s private information, such as their Wallet information, and send all of that data to the attacker.
What about the privacy breach?
So, nasty stuff that TikTok claims to have fixed, and those vulnerabilities could just be honest mistakes and all around lack of focus on building secure software. Not necessarily a shocker.
Separate from these types of vulnerabilities, however, is that TikTok is being accused of spying on its users.
We talked about that fine they received for being weird with kids’ data and there have been other reported issues with TikTok violating user privacy.
So TikTok, in April, said that it would stop this kind of behavior, except now they’re being accused of spying on their users, again!
Beta testers for the upcoming iOS 14 software for iPhones found that TikTok was recording what users are typing on their phones, which could range from non-sensitive information to passwords or even sensitive emails.
This has to do with how iOS’ clipboard function works, which essentially lets any app record all text and images that were copy-pasted via the clipboard function without notifying or warning the user.
This means they could see your passwords, emails, messages, financial information, etc…
TikTok commented on the matter, according to the Forbes article, saying that the issue is “triggered by a feature designed to identify repetitive, spammy behavior” and that it has “already submitted an updated version of the app to the App Store removing this ‘anti-spam feature’ to eliminate any potential confusion.”
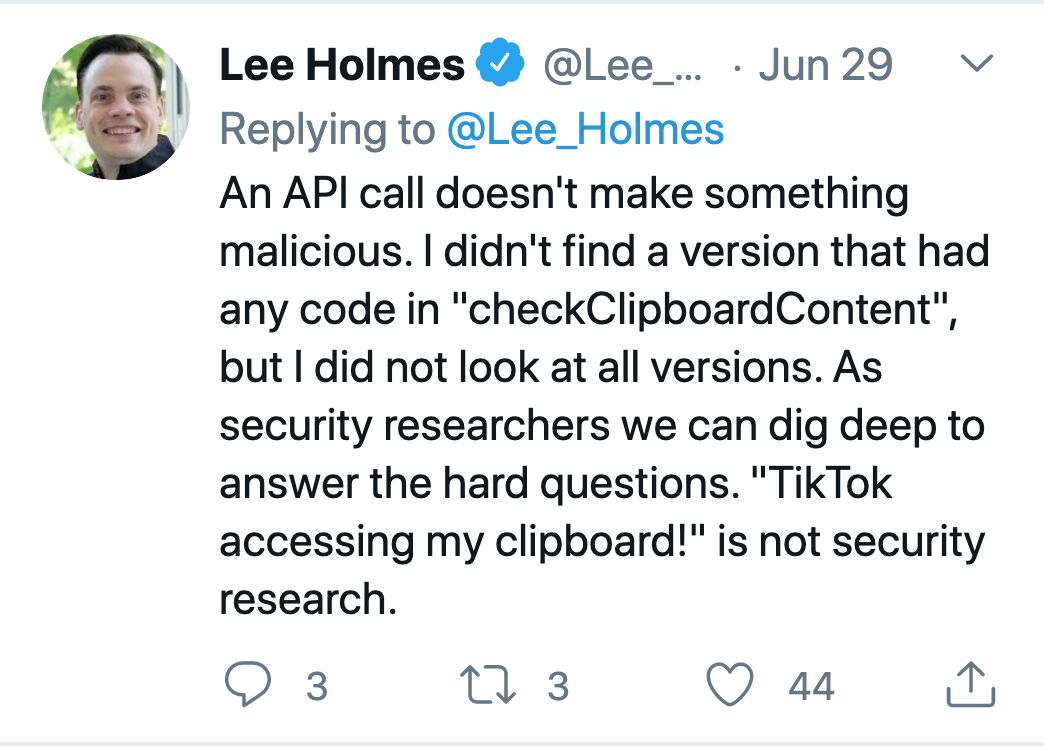
However, Lee Holmes tweeted that the versions they checked of the Android APK had no code in the checkClipboardContent() method, making it unlikely that the clipboard issue was part of a malicious attempt by TikTok, and rather just an oversight.
The verdict about TikTok spying and security issues…
So, are they willingly spying on their almost billion users? Were the backdoors and vulnerabilities there on purpose or simply as a result of oversight? Let us know what you think in the comments below!
And while we might never know the truth, one thing’s for sure: I’m not installing or using TikTok any time soon, and not just for the reasons mentioned in this video.












Responses