Initialization Vector (IV) attacks with WEP
Understanding Initialization Vector (IV) attacks is important for the CompTIA Security+ exam, but it can be confusing if you’re not as familiar with cryptography concepts. In this post, we’ll explain what an IV is, how it’s used to encrypt data, what IV attacks are, and how to defend against them.
What are Initialization Vectors (IVs) for anyway?
When it comes to encrypting data, there are many different types of encryption. Some are more effective than others, and some are more complicated than others.
There are even different ways of encrypting blocks of information, and we call those different methods modes of operation.
Some approaches involve using something called an Initialization Vector (aka IV). The IV is combined with the secret key in order to encrypt data that’s about to be transmitted.
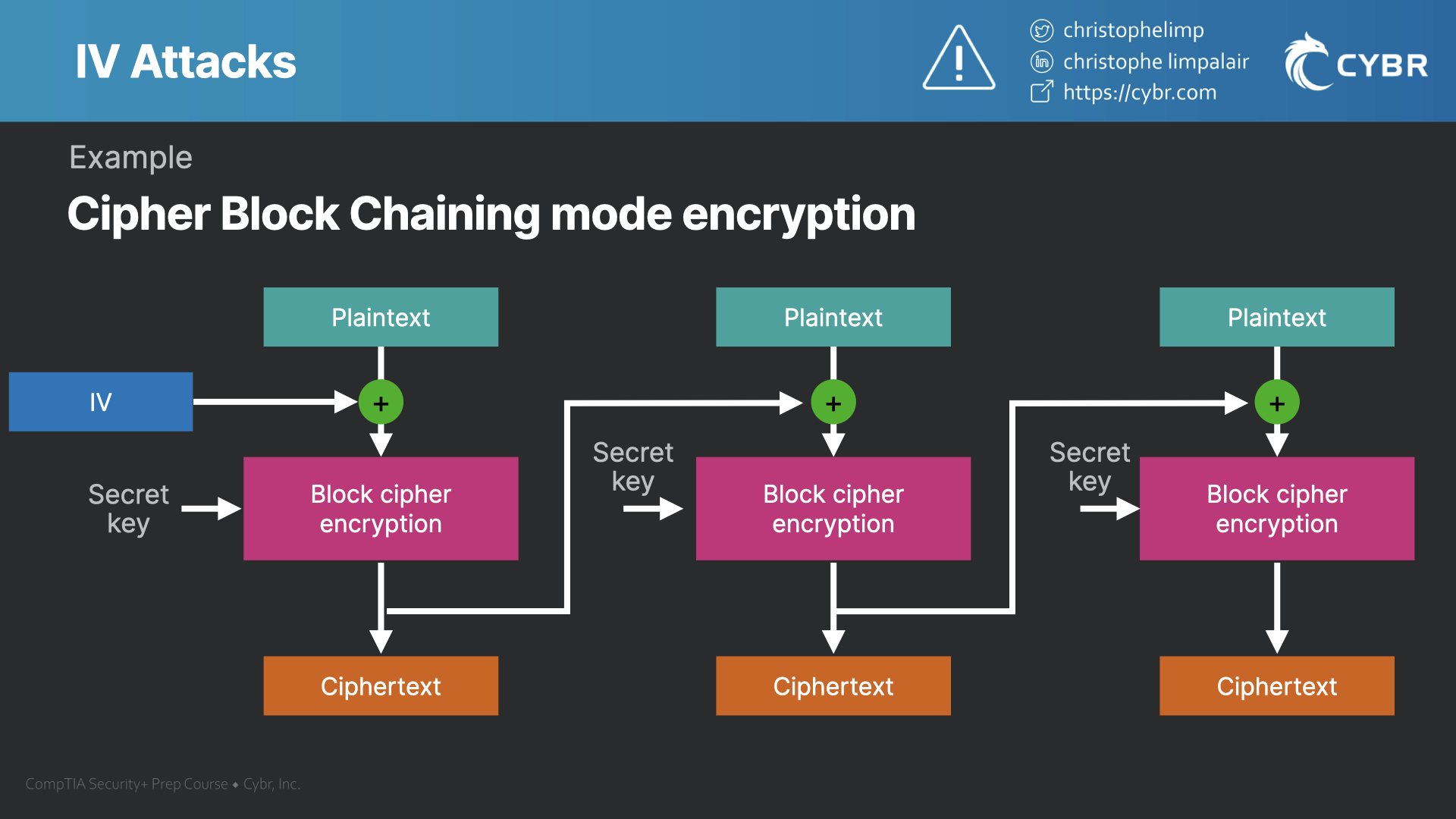
Just before encryption occurs, we add the initialization vector, or IV, and it adds extra randomization to the final ciphertext. Then, on the second block of data, we use the resulting ciphertext as the IV for the next block, and so on.
This is important because it ensures that even if we’re using the exact same plaintext and secret key more than once, the resulting encryption will look different every time. This also makes it much more difficult for an attacker to reverse engineer a network’s encryption, even if they were able to gain access to plaintext information.
What are IV attacks?
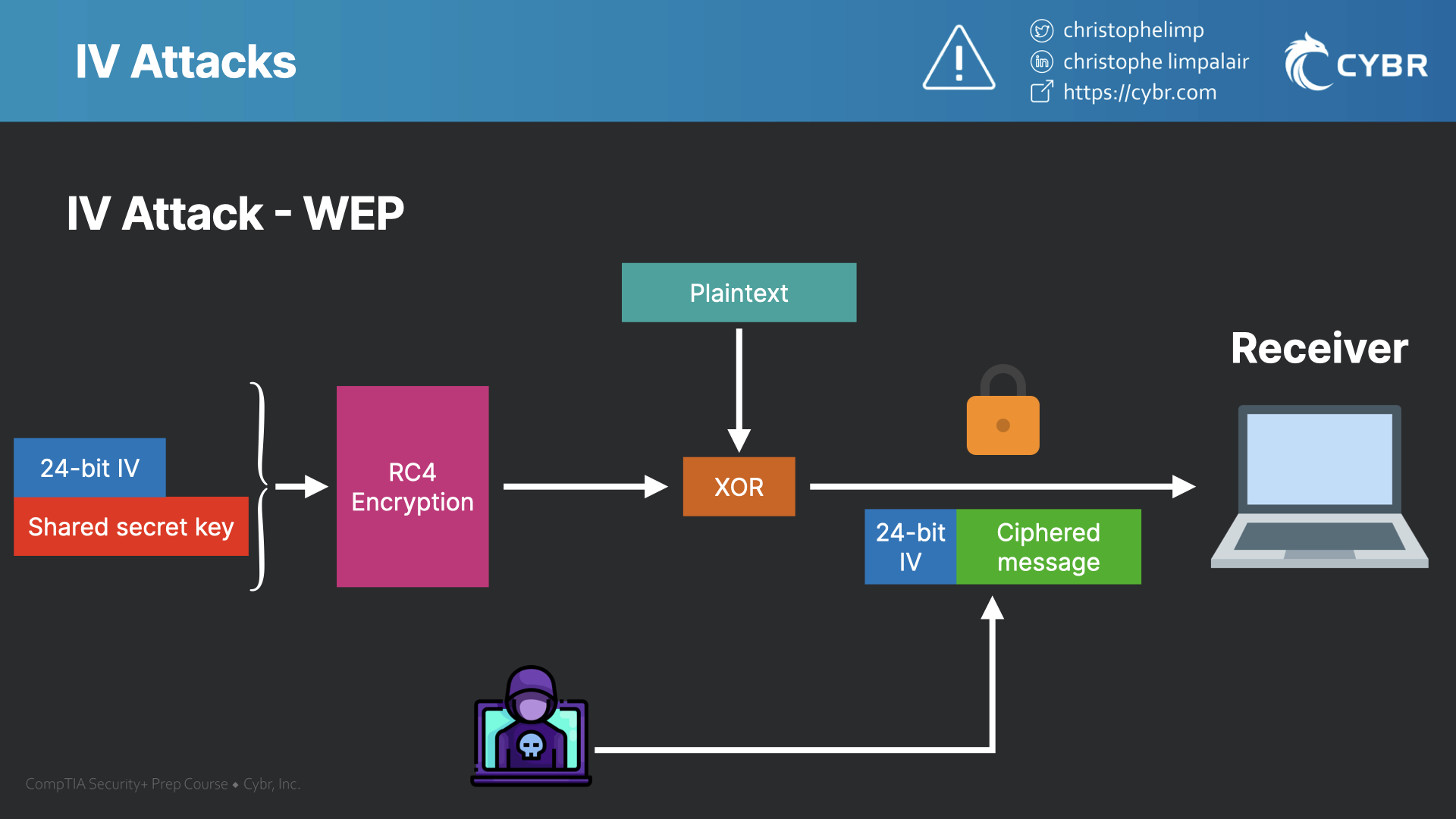
There can be some situations where an IV attack can overcome the protection that we just talked about, and end up allowing an attacker to figure out the secret key being used. More modern wireless protocols like WPA2 and WPA3 prevent this from happening, but WEP was vulnerable to this attack.
Because WEP uses 24-bit IVs, which is quite small, IVs ended up being re-used with the same key. Because IV keys are transferred with the data in plaintext so that the receiving party is able to decrypt the communication, an attacker can capture these IVs.
By capturing enough repeating IVs, an attacker can easily crack the WEP secret key, because they’re able to make sense of the encrypted data, and they’re able to decrypt the secret key.
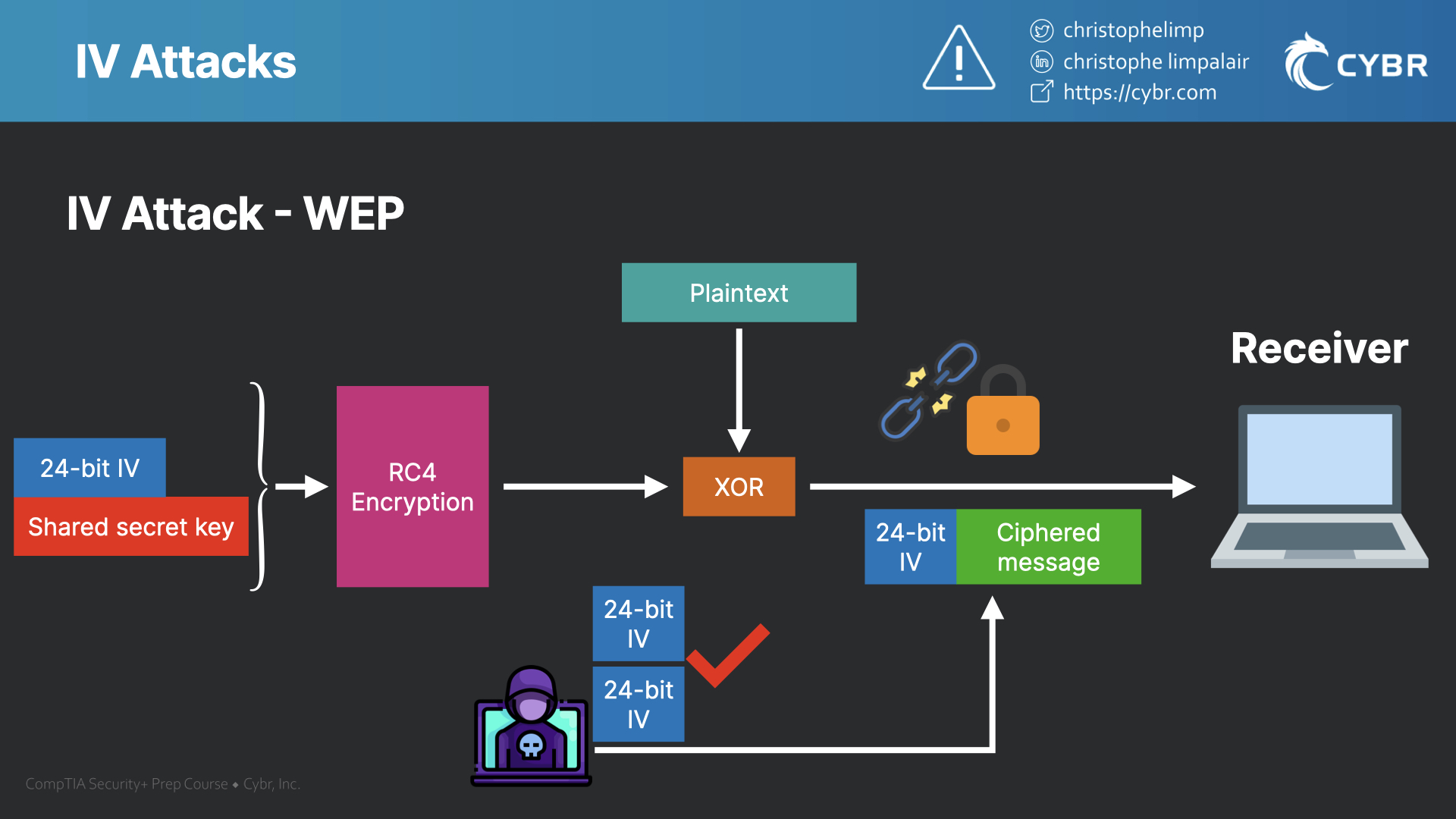
This is one of the many reasons that WEP was deprecated and replaced with much more secure wireless protocols.
Defenses against IV attacks
Defending against IV attacks comes down to using more secure wireless protocols such as WPA2 or WPA3. WEP was deprecated a while ago, and WPA is considered less secure than WPA2, so both should be avoided.
WPA2 and 3 use 48-bit IVs instead of 24-bit IVs, which may not sound like much, but it adds a massive number of new potential IV combinations as compared to WEP, which makes it far less likely to repeat.
That’s not the only reason that WPA2 and 3 are stronger than WEP, but it certainly does help. We’ll review some of the other reasons in a future blog post and in our CompTIA Security+ preparation course.
Studying for the CompTIA Security+ Exam? Enroll in our course or practice exams!








Responses