New Course: Beginner’s Guide to sqlmap

One of our most popular and requested content categories has been regarding SQL injections and the popular tool sqlmap that is used to help find SQL injection vulnerabilities. Following a number of questions about how to use sqlmap from students who enrolled in our Injection Attacks: The Free Guide course, we figured that the easiest way to help answer those questions was to create a short course on how to get started using sqlmap for beginners.
So, this past week, we did just that and launched our latest course: Beginner’s Guide to sqlmap, as well as an Ebook version:
This course was intentionally kept short in order to be laser-focused on one simple goal: getting beginners up and running with the sqlmap tool. We do that covering these topics:
- Setting up a home lab environment
- Downloading and installing sqlmap
- Exploring the most useful sqlmap options and configurations for beginners
- Finding and exploiting your first SQL injection with sqlmap
- Extracting passwords from a database
Let’s take a closer look at what each of those steps entail in the course.
Setting up a home lab environment
When you’re learning tools, there’s absolutely no substitute for getting your hands dirty and practicing what you’re learning. sqlmap is no exception. So, before we even dive into the course, I show you exactly how to create your own home lab environment for free.
There are a bunch of different ways to create your own home labs, but we keep it simple and limit it to these technologies:
- Virtualbox (to create our virtual machine)
- Kali Linux (the operating system)
- Docker (the container system to run our vulnerable environment)
- DVWA (Damn Vulnerable Web Application)
- sqlmap
Downloading and installing sqlmap
While Kali Linux comes pre-installed with sqlmap by default, there are a couple of reasons I still show how to download and run sqlmap in your home lab environment.
The first reason is in case you aren’t using my home lab environment setup, and whatever setup you are using doesn’t come with sqlmap pre-installed by default.
The second reason is because you may want to use the latest version of sqlmap, which Kali won’t include. Kali will include the latest stable version, but not the dev version. The dev version will have the latest features which might attractive to some, even if it might also include some new bugs that haven’t been fixed yet. So it’s a tradeoff that you should consider, but I wanted to give you either option.
So technically speaking, you could skip this lesson and still be able to complete the course 100%, but I like to give options.
Exploring the most useful sqlmap options and configurations for beginners
sqlmap is feature-rich and has a ton of options. While this is fantastic for professionals, it can definitely be intimidating for beginners. For that reason, I narrow down the scope of this course to some of the most useful features and configurations for beginners to use when they’re trying to find their first SQL injection. Those features are:
- Target
- Request
- Enumeration
- Wizard
Target
Target is used to tell sqlmap which target to go after. Is it a single URL target? Great, use the -u or --url options to specify that URL.
Request
Once you’ve defined a target, you need to tell sqlmap how to craft its request to the application. Does it need to send any data with the request (ie: for a POST request)? If so, you can specify that with --data=DATA.
Or maybe you need to pass in cookie information. For example, with the DVWA environment, you need to authenticate into the app before you can attack the vulnerable endpoints. So if you don’t pass in authentication cookies to sqlmap, it will simply get redirected to the login page. You can pass in cookie information to sqlmap with --cookie=COOKIE.
Enumeration
The enumeration features are where things start to get interesting. Once you’ve crafted your target and request, you need to give sqlmap specific instructions. Because even if it finds a SQL injection vulnerability at that endpoint, what should it do?
Here we can do things like:
- Return the current user that the application is using to make requests to the database (
--current-user) - Return a list of the databases’ tables (
--tables) - Get the database scheme (
--schema) - and a whole lot more
This feature section has a lot of power and comes in very handy once sqlmap has found an entrypoint.
Wizard
While we don’t end up using the wizard feature at all in this course, it still is an excellent feature for complete beginners, and so I had to mention it in the course. If you find that I’m moving too quickly through concepts, features, and functionality, you can always fall back to the wizard option.
The wizard essentially guides you through what sqlmap needs to successful attack a target. So instead of trying to figure out which options you should feed into sqlmap for it to be successful, sqlmap will tell you line-by-line what it needs, and just as importantly, it will ask you to pick certain options and it will show you which of those options are defaults.
For example, this is what it looks like:
Please enter full target URL (-u): http://localhost/
POST data (--data) [Enter for None]: Enter
Injection difficulty (--level/--risk). Please choose:
[1] Normal (default)
[2] Medium
[3] Hard
> 1
Enumeration (--banner/--current-user/etc). Please choose:
[1] Basic (default)
[2] Intermediate
[3] All
> 1
sqlmap is running, please wait..Code language: JavaScript (javascript)So a helpful feature for beginners that I had to mention, but that I help you get past pretty quickly in the course so that you can move faster and perform more advanced attacks down the road.
Finding and exploiting your first SQL injection with sqlmap
After we get through the steps of creating our home lab, choosing the version of sqlmap that we want to use, and then a quick walkthrough of some of the most useful features, we get to work finding our first SQL injection vulnerability, and then exploiting it.
This is the first time we perform an actual attack against the vulnerable environment (in this case, the DVWA). We use everything we’ve learned in the course so far to craft our payload, and then go from there.
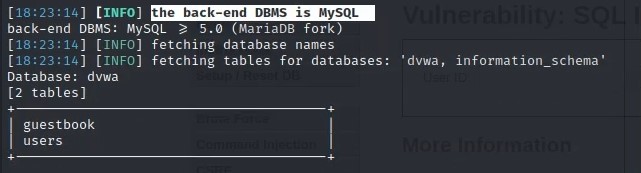
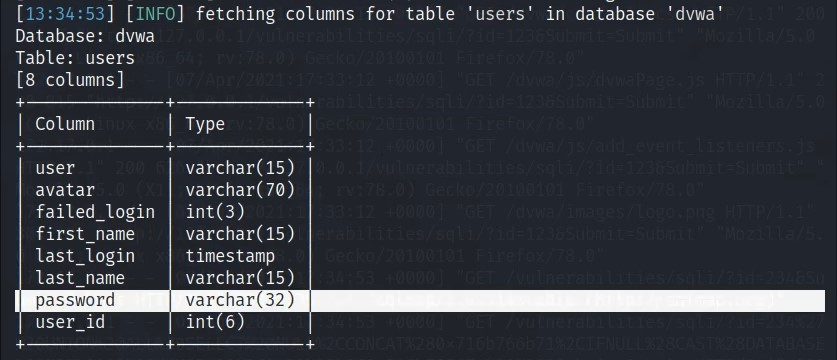
This means that we use a combination of the Target, Request, and Enumeration features to craft a successful payload and return a list of all the tables contained in the vulnerable database. We then change our payload to enumerate the database schema so that we can see how the database is structured.
By the end of this lesson, we’ve found an important piece of information: the database contains a table named users, which is highly likely to contain password information.
Extracting passwords from a database
I felt like this course would not have been complete without doing something pretty cool beyond just listing information from the database structure. The other reason I wanted to include this lesson is because I wanted to showcase just how devastating SQL injections can be when they’re not taken seriously.
Of course, in the real world, the stars have to line up in order for you to be able to take it this far, but it’s happened for more times than it should have, and again, this lesson is a reminder of that.
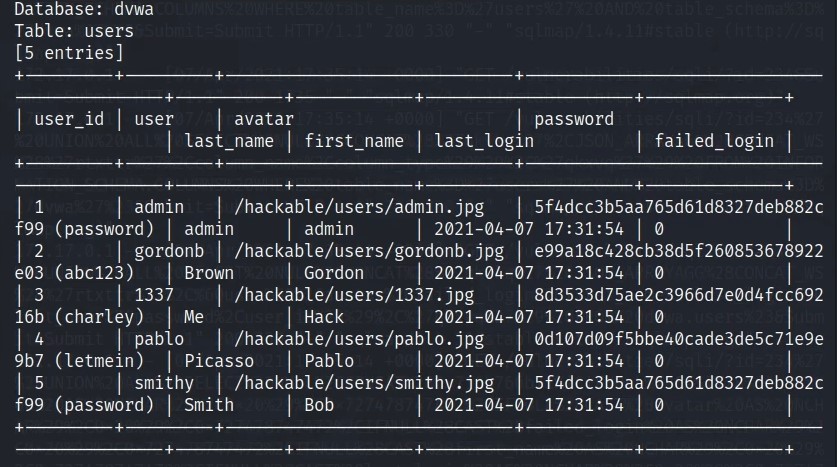
In any case, using information from the prior lesson, we craft a different payload that specifically targets the users table.
We:
- Verify that the
userstable does indeed contain password information – hashes of passwords to be exact - Enumerate the
usersdata - Feed the password hashes into sqlmap’s built-in password cracker
- Perform a dictionary-based password attack
- Crack all of the password hashes contained in the
userstable to plain text
We then try to enumerate the database management system user passwords (the database administration users, not the application’s users) using the --passwords enumeration option, but it fails. The user that we are assuming through the application simply doesn’t have the required permissions to pull this off, which is a great reminder that the real-world may sometimes have vulnerabilities, but exploiting those vulnerabilities can be an entirely different beast that requires even more patience and perseverance to overcome 🙂
Guide to sqlmap Conclusion
The hope is that this course becomes a helpful stepping stone for those looking to learn sqlmap and to be more well versed in the art of SQL injections. Beyond that, we’ve started working on a new course: sqlmap Deep Dive which will go to the next level and take a much deeper look at what sqlmap has to offer, and how it can be used in the real world to find vulnerabilities: whether with black box, grey box, or white box testing.








Learning about SQL injections and sqlmap? Join our Discord community to ask questions and collaborate with others: https://cybr.com/discord
Yes this course is solid i tried so many out there, and they are just boring at least this straight to the point. Can you make a course on how to write a solid report regarding SQLInjection and or Command Injection ?
That’s a great suggestion! Adding to our content roadmap!
SQL Injection and Command Injection are the gold mines i need more time on.