Hashing use cases

In practice, what is hashing used for? How is it being used in the real world? Let’s take a look at a few common hashing use cases.
By the way, this article is pulled directly from one of our lessons in Cybr’s CompTIA Security+ SY0-601 Course where we provide you with all of the knowledge you need to pass your certification exam.
What is hashing?
Before we dive into the use cases, we first need to understand what hashing is.
Hash functions are basically just really good randomizers of data. You feed an input to a hash function — like let’s say a password — and it outputs a mathematically random output that won’t have any recognizable structure that would reveal what the original input was. This output is called a hash value, fingerprint, or a message digest.
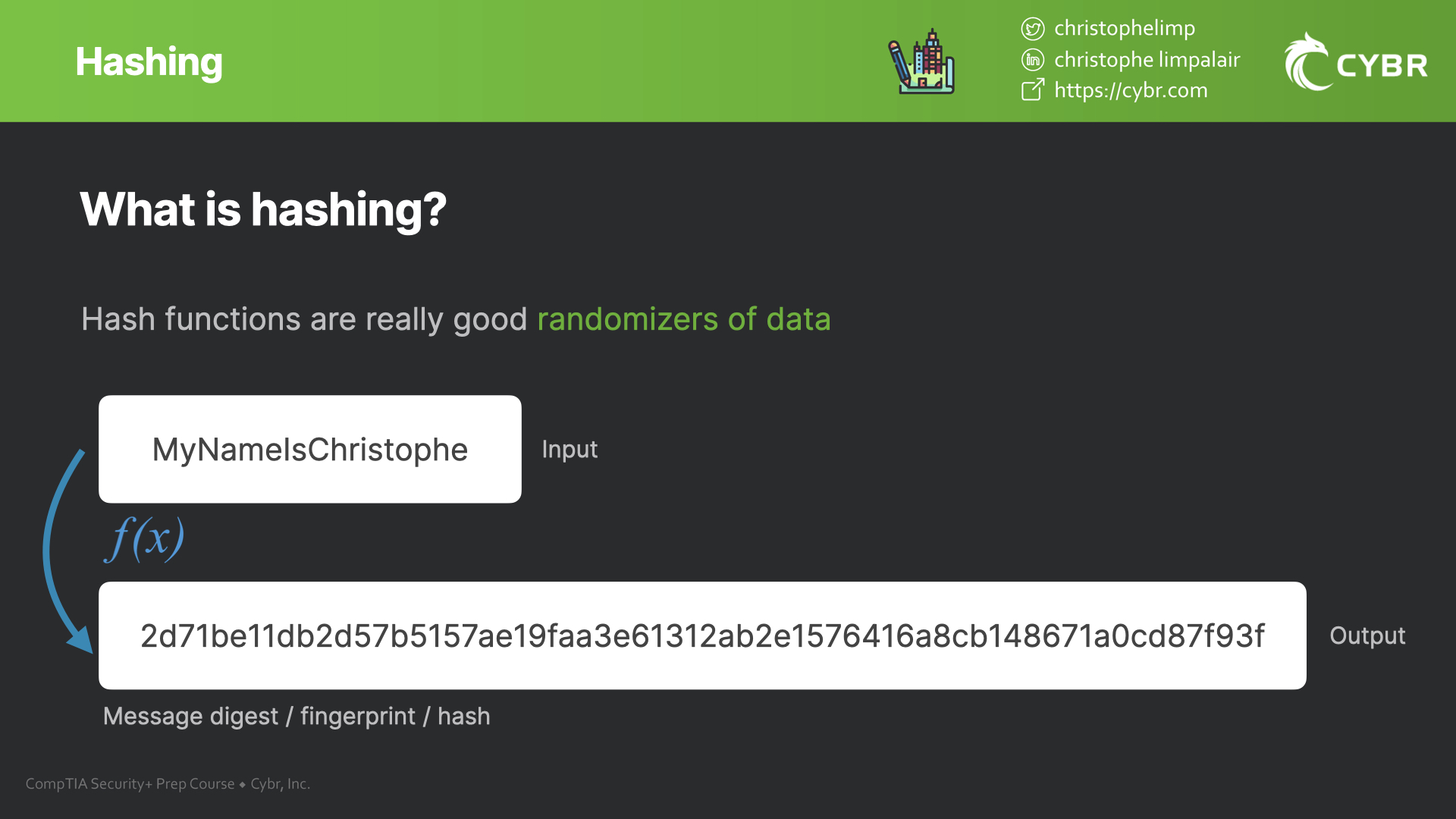
Hashing is a one-way trip, unlike encryption. Once you hash input, you can’t recover it from the output. This also means that hash functions don’t have a decryption key. It’s simply a code algorithm that everyone can use.
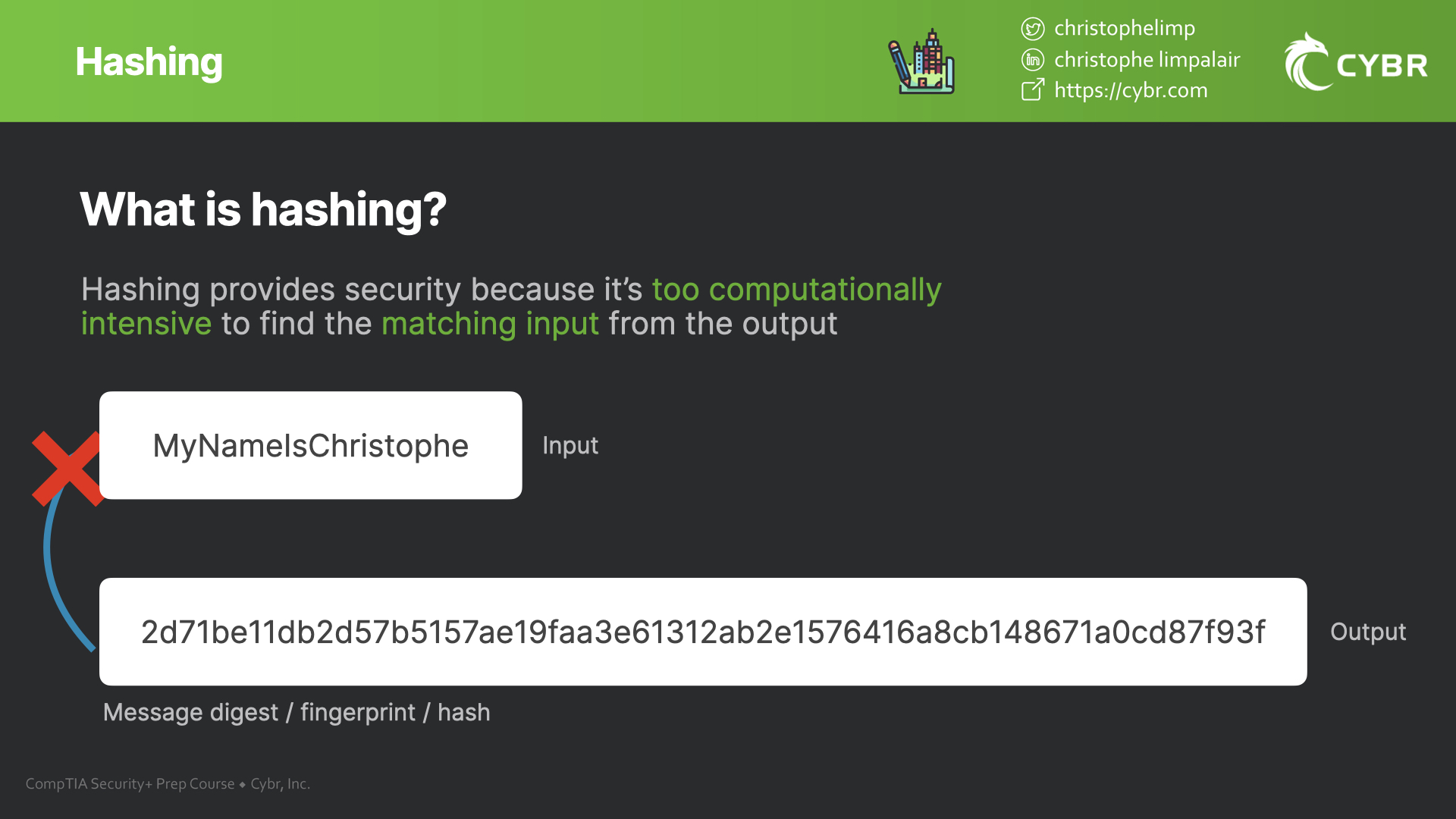
Even though everyone can see how it works and everyone can understand the process, hashing still provides security because it would be too computationally intensive even with the most powerful computers in the world to compute the matching input from the output.
Because hashing produces a fixed length output (regardless of the size of the input) it does mean that it’s a mathematical certainty that collisions* exist for every hash function, but again, it is practically impossible to find these collisions given a strong enough hash function.
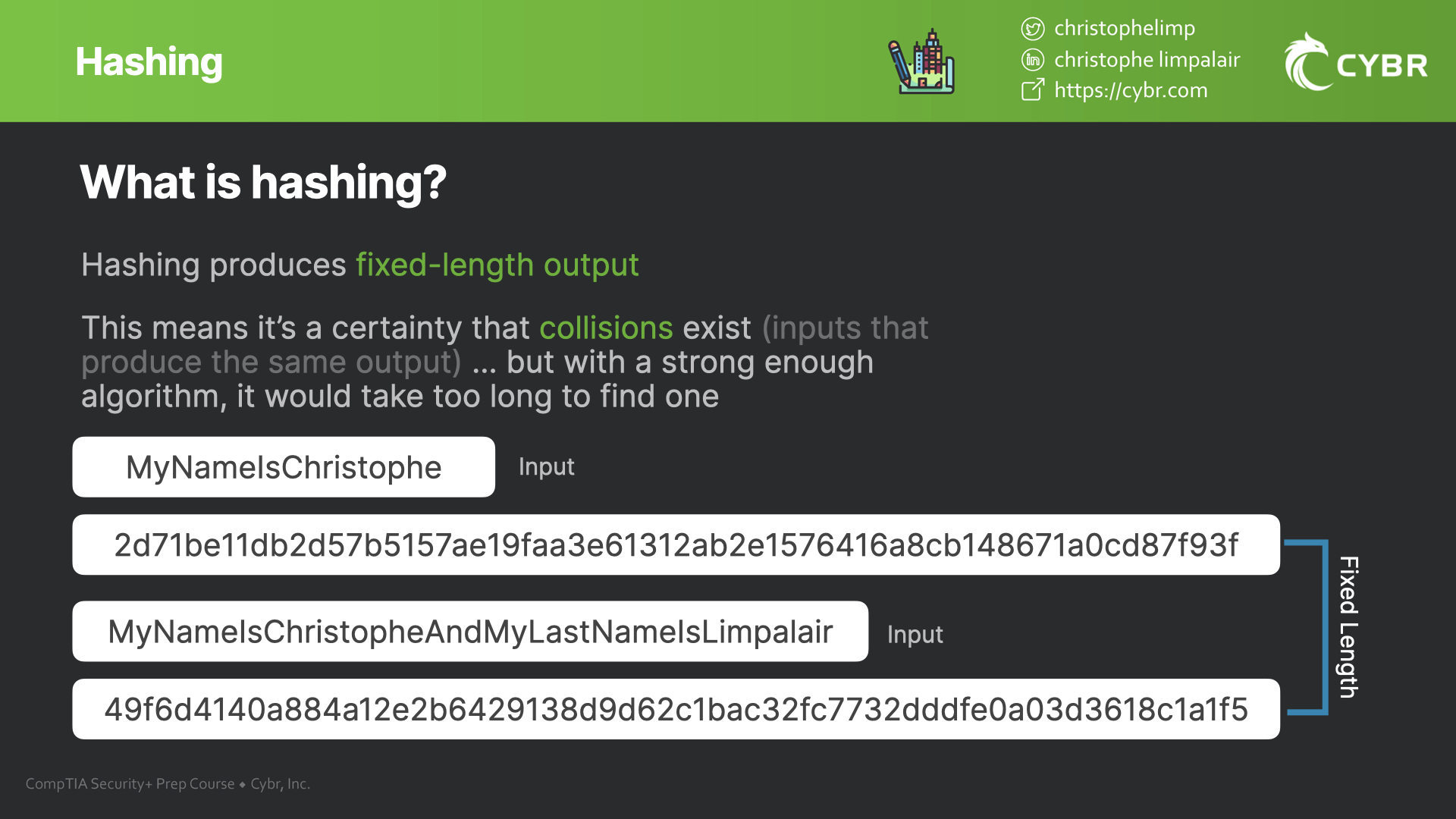
*A collision is what happens if two different inputs were to produce the same output. Why would this be a problem? Let’s take a look with the first hashing use case: hashing for password storage.
Hashing for password storage
As we talked about in our article “Encrypted versus hashed passwords. What’s the difference?” instead of storing the actual password, or even an encrypted version of a password that could be decrypted, applications store the hash output of that password.
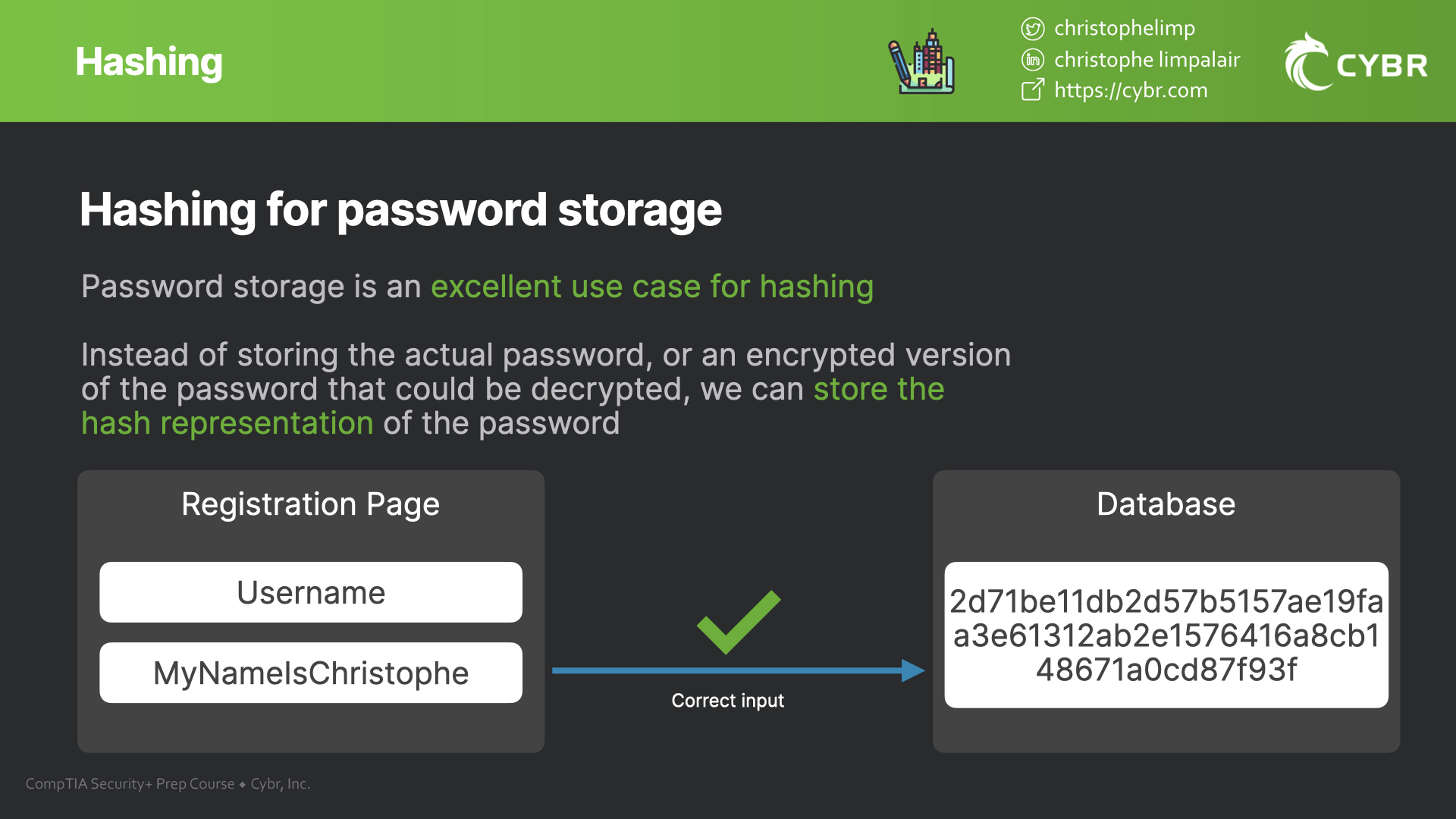
Even if a malicious actor gained access to your database, or a rogue employee were to look at that database, all they would see would be hashed values. If they tried to use those hash values to login, it wouldn’t work because the output of those hash values would not match the application-stored values.
They also wouldn’t be able to decrypt those hash values (since it’s a one-way trip, remember?)…which means those values would be useless to an attacker even if they got their hands on them unless they were able to crack them.
Hashing for file download signatures
Hash values can also be used to verify file integrity.
As you download files from the Internet, you’ll sometimes notice that the download page includes a hash value. The point is to compare your downloaded file’s hash value with the hash value on that website, because if someone tampered with your download in some way, then the download would have a different hash value.
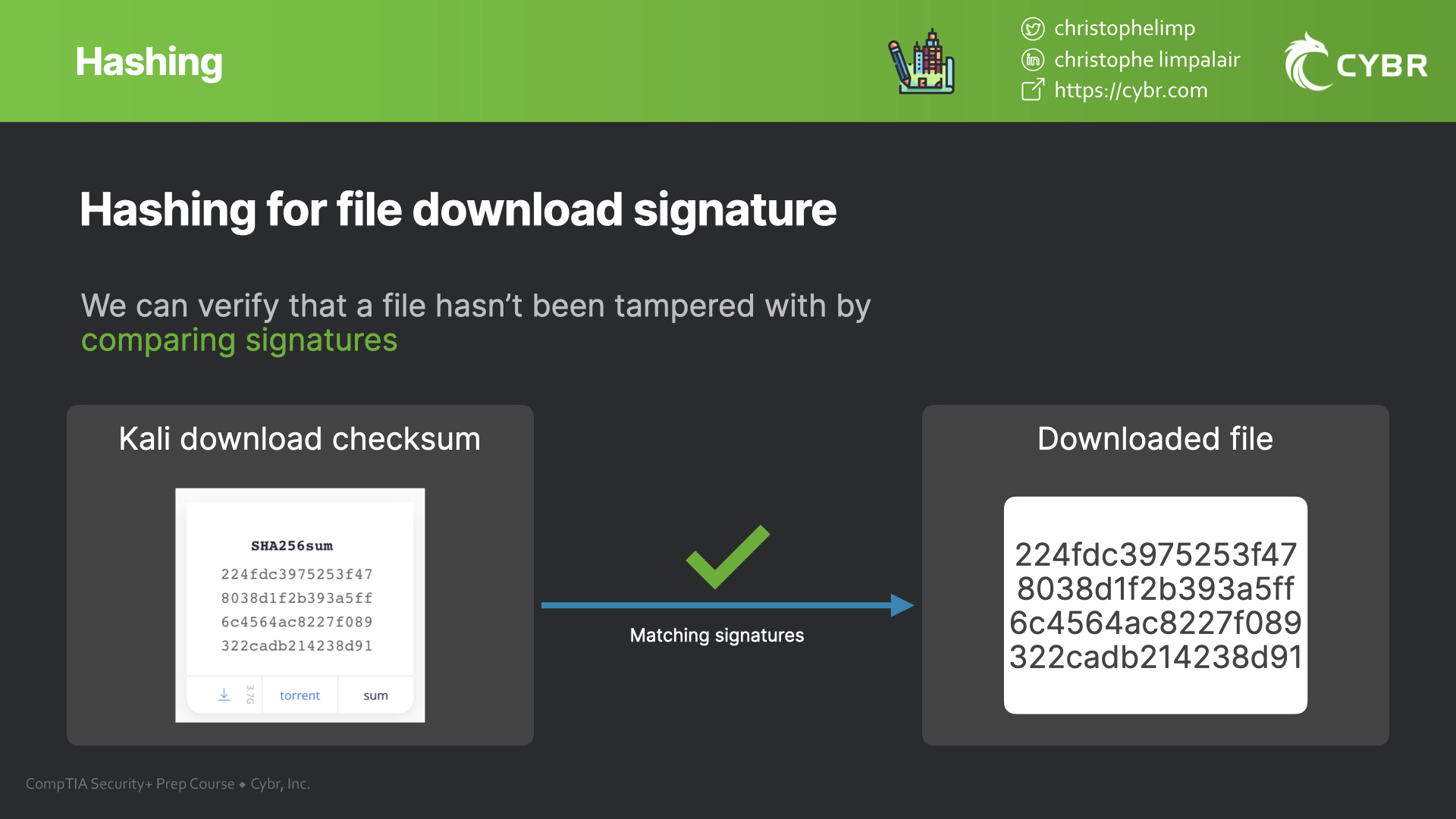
If that were to ever happen, you should not open the download, and instead you should report it to the organization hosting this file. Because either they forgot to update their hash value or someone tampered with your download.
See how this works and how to build a quick Python script to check file hashes.
Hashing for digital signatures
Hash functions make important building blocks for other algorithms. In fact, hashing is one of the core elements of a digital signature system. Because hashing provides a fixed-length output, that output can then be used as part of an encryption process.
Digital signatures can be used to verify the origin of data, and to verify data integrity. It can also be used for non-repudiation, which is when you need to provide proof of delivery and proof of the sender’s identity so that neither party can deny having processed the information. This is very useful for contracts, for example. (“Your honor, I didn’t sign that document!” “Yes you did, here’s the proof!”)
To create that digital signature, we can combine both hashing and asymmetric encryption. For example, let’s say that I need to send you a digitally signed document. I could create a hash of the document, and then encrypt it using your public key. That would be the digital signature that I send to you alongside the original document.

After receiving the document and my digital signature, you would use your private key associated with the public key to decrypt this signature that I sent you.
You would then have access to the original hash value that I created and encrypted. Using the document you received, you would generate your own hash value (using the same hash function) and then compare it with my hash value that I sent you. If the two hashes match, then you know that the digital signature is valid. If it doesn’t match, it means you have a signature that has been tampered with.
This is an example of using hashing with encryption for verifying digital signatures.
Conclusion
As you can see, while the concept of hashing is relatively simple, it’s very versatile and serves an important role in securing data. These are just a few examples of what hashing can be used for, as there are many others…but hopefully this gave you a better understanding of what hashing is and how it works.
If you’re still fuzzy on some of the differences comparing hashing and encryption, be sure to check out our article that deep-dives into their differences.
Have another hashing use case we didn’t cover above? Share with us in the comments!






Responses