New course: The Practical Guide to sqlmap for SQL Injection

Ever since launching our Injection Attacks: The Free Guide course, we’ve received numerous requests to continue building SQL injection-related content, including how to use the popular automation tool sqlmap.
So, this week, we delivered! We’ve officially launched The Practical Guide to sqlmap for SQL Injection in Early Preview. The main goal of this course is to teach you how to use this powerful tool for professional engagements such as pentests or bug bounty hunting.
With that, let’s take a closer look at what this course covers and how it’s structured!
One quick thing…
Before moving on, I also want to mention that we donated 40% of all course sales for 3 months following the course’s launch directly to the sqlmap open source project in order to support its development and maintenance.
A lot of companies talk openly about how they support open source, which is great, but we put our money where our mouth is. Cybersecurity (and let’s be honest, IT as a whole) would not be what it is today without hours upon hours of hard work from individuals who believe in making their work open source. This is just one of our ways of saying thanks for building such a wonderful tool, and of offering our support.
Another quick thing…what’s Early Preview?
This course launched in Early Preview, which means a significant portion of the course had been uploaded, and we continued to release brand new content every single week until the entire course is complete! We do this so that you can enroll early on at a discount, and you get all of the updates and new content on a weekly basis until the course is 100% complete.
High-level overview of the course
As mentioned, the main goal of this course is to teach you how to use sqlmap for professional engagements such as pentests or bug bounty hunting. To do that, we need to go beyond just the high-level basics of explaining a few options and how to issue a few commands.
Instead, we need to take a deep dive look. That’s exactly what we do in this Practical Guide to sqlmap for SQL Injection course.
We not only explore payloads that sqlmap uses under the hood, but we take a look at the various SQL injection techniques and their implementation. We take a look at the source code repository, how it’s structured, how to find some of the most important files and configurations, and how to modify those configurations depending on your needs.
We explore every single option that sqlmap provides from top to bottom, with examples and explanations of how they work and when to use them effectively. We even practice using many of these options in our own home lab environments so we can see exactly what’s going on and what the results are.
Then, once we’ve covered all of the available options, we walk through example scenarios that combine what we’ve learned up to that point. This is where you can really start to see how sqlmap’s options, configurations, and features all work together.
We also take a practical look at a question most students have: how can I use tools like sqlmap when most applications are protected by a Web Application Firewall (WAF)? We examine built-in functionality meant to detect WAFs, we go back over specific and niche options that can help, and we explain tamper scripts as well as how to effectively use them. Tamper scripts are designed to bypass WAFs, IPSs, and other security controls, so they’re an important part of using and understanding sqlmap.
Finally, we also explore how sqlmap can be used as an API.
How the course is structured
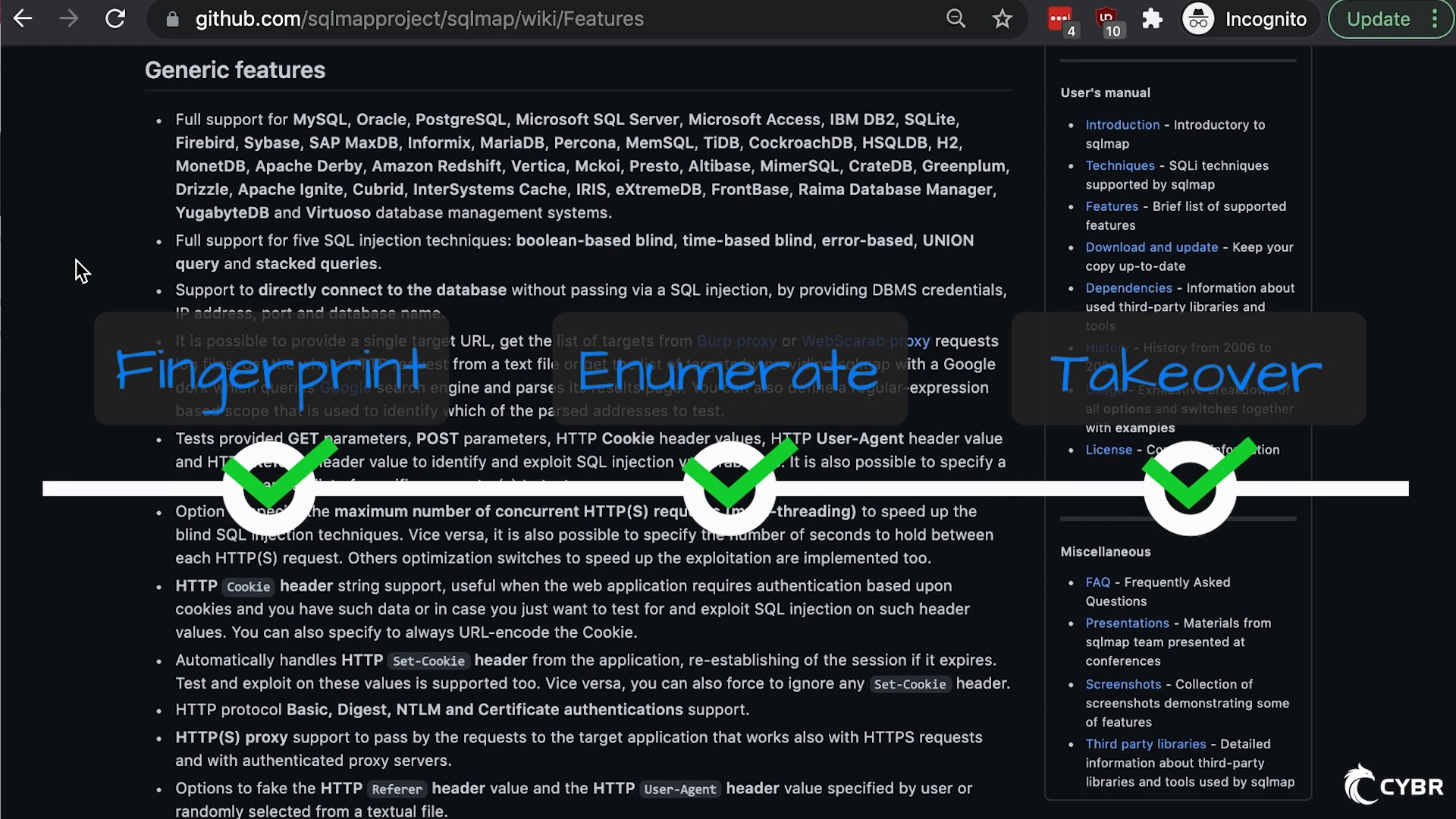
Similar to how sqlmap has 3 main phases (fingerprint, enumerate, takeover), this course has 3 main sections:
- Getting Started
- Options Deep Dive
- sqlmap in Action
Getting Started
This section includes everything from “about the course” and “about the course author” to “creating a home lab environment” and an overview of sqlmap.
The lesson dedicated to creating a home lab environment shows you how to download and install VirtualBox and Kali Linux on your own computer. This then sets you up to download any tool, file, and testing environment that you’d like.
For example, we quickly download Docker which enables us to spin up testing environments in containers. This is extremely practical, fast, and easy, because all you need is a couple of commands to spin up and tear down those environments whenever you need them.
The lessons under the “sqlmap Overview” sub-section start by giving a quick overview of what sqlmap is. Chances are that if you’re interested in this course, you already have a rough idea of what sqlmap is, but we take a closer look.
Then, we explore the different SQL Injection techniques that sqlmap uses under the hood:
- boolean-based blind
- time-based blind
- error-based
- UNION query-based
- stacked queries
While we don’t have time to teach those techniques in-depth in this course (we already cover them in the Injection Attacks: The Free Guide course), it is important to understand how sqlmap specifically implements these techniques, since it can change your engagement’s outcomes.
We then talk a bit more about sqlmap’s 3 main phases:
- Fingerprint
- Enumerate
- Takeover
The first two — fingerprinting and enumeration — are critical to understand for all sorts of engagements. The 3rd is typically not going to be allowed in bug bounty engagements, but could still be allowed for some types of pentest engagements, and/or if it’s for your own company’s applications. It can also, arguably, be the most fun part 🙂
We learn what fingerprinting means in the context of sqlmap, and what we can expect from this page. We then learn what enumerating means in the context of sqlmap, and what we can expect from that stage, and so on.
After that, we walk through sqlmap’s source code repository in order to understand how the source code is laid out, and more importantly, where to find what you need. Whether you’re looking for sqlmap’s injection payloads, configuration files, tamper scripts, or included third-party tools, I show you exactly where to find that information. I even have cheat sheets that will help you navigate sqlmap’s source code structure and help you narrow it down to some of the most important directories. We’ve got a few more sqlmap cheat sheets here.
Finally, at least in this section, we learn how to find and use a vulnerable server (vulnserver.py) included with sqlmap to test out options and scenarios.
Options Deep Dive
This section is the heftiest section of The Practical Guide to sqlmap for SQL Injection course. The reason for that is because we cover literally every single one of sqlmap’s options, and there’s a lot of them. Some of them are critical to use, while others serve narrow and specific purposes. Regardless, if you want to truly master sqlmap, you’ll need to know what purpose they all serve and how to properly use them.
This is also where the “Practical Guide” portion of the course’s name comes from. Not only will I teach you how to use these options, but I hope these lessons can serve as practical guides that you can pull up whenever you need help in your engagements. Remember that sqlmap can do this thing you need for this particular engagement, but don’t remember how to use that option? No problem, just pull up the course and go straight to the relevant lessons!
You’ll learn everything from how to set targets (either from a single URL or from Burp/ZAP log/request files), how to craft requests with the needed headers, methods, data, cookies, authentication, csrf tokens, etc… to using sqlmap anonymously in order to evade Blue Teams, writing custom Python code to change data and requests on the fly, use tamper scripts effectively to evade security controls, fine-tune the exact SQL injection techniques you want sqlmap to use, enumerate and extract data contained in databases, and perform takeover actions such as injecting user-defined functions in databases.
Honestly, this section probably contains way more information than you ever wanted to learn about sqlmap…but that’s how you build practical skills, my friend.
sqlmap in Action
Once we’ve looked at literally every option sqlmap offers, we move on to another practical section of the course: sqlmap in action.
This section goes through a variety of scenarios designed to mimic what you might expect to encounter in pentests or bug bounty engagements, which forces us to use everything we’ve learned up to that point.
That means we’ll use options we’ve learned about to go through all 3 of sqlmap’s main phases (fingerprint, enumerate, takeover) against target environments. This is where you get to see it all come together, and where you get to practice chaining multiple options and commands together.
After that, we have a sub-section dedicated to bypassing WAFs, since that’s one of the most commonly asked questions. This is a challenging topic to cover because bypassing WAFs is no easy feat and does require patience. There are professionals that dedicate a portion of their careers to this topic alone, and I’m by no means a WAF expert. With that said, sqlmap not only include built-in functionality to detect WAFs, but it also uses 3rd party tools to help detect and evade them. As we talked about, we can also make use of existing tamper scripts, or create our own.
Those are all things we look at.
Finally, and to wrap up the course, we have a sub-section dedicated to running sqlmap as an API. We’ll take a look at why and how.
Ready to learn how to use sqlmap in-depth?
I’ve had a lot of fun creating this course, and I hope to see you there! Don’t hesitate to reach out if you have any questions, but otherwise, you can enroll by clicking below:











i’m not a locate user, could i buy your course by other method?
Hi! The best way to buy our courses is via credit card. We use a payment gateway that works globally, so as long as you have a credit card, you should not have any issues!
i have buy with discord. Thnaks!
Yay! Thanks for your support!